WannaCry.exe - An Analysis
The final course objective of Matt Kiely’s Practical Malware Analysis & Triage was to create a triage report for any sample in the course.
I chose the WannaCry Ransomware.
Executive Summary
| HashType | Sum |
|---|---|
| sha256 | 24D004A104D4D54034DBCFFC2A4B19A11F39008A575AA614EA04703480B1022C |
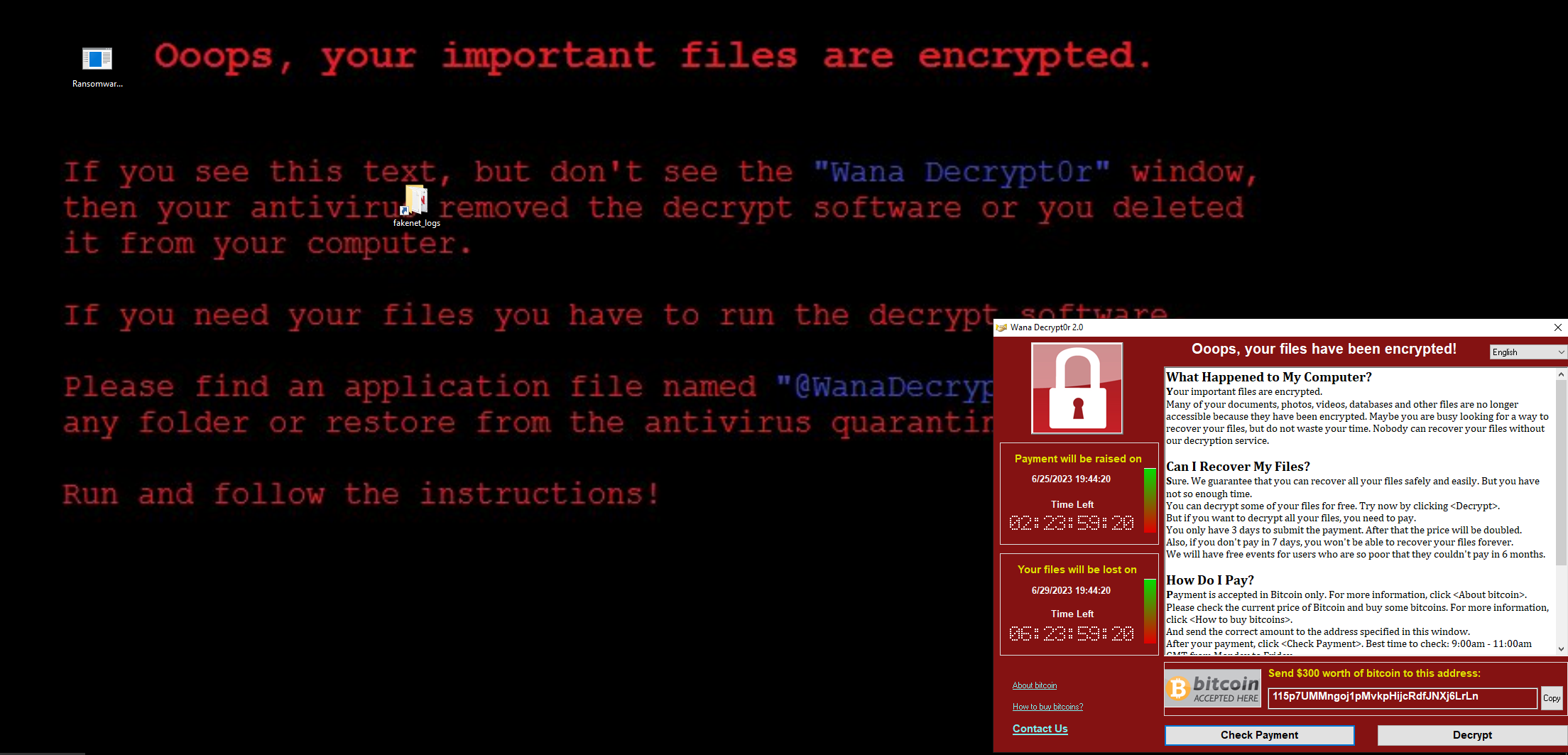
WannaCry.exe is ransomware that appeared in 2017. It consists of one executable that contains several other binaries in it. Once executed with Administrative privieges, the ransomware begins encrypting the files on the victim’s storage. WannaCry also attempts to reach out to other hosts on the netork via SMB and attempts to infect them. Once infected, the host will begin seeing a changed background and message dialog alerting them that their files have been encrypted and where they can send payment if they want them decrypted.
The YARA rule to identify WannaCry.exe is the last section of this report.
High Level Technical Summary
"Execute as Administrator" -> Check www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com/
If "Host can resolve address" then
--> [Yes] "Do nothing"
else
--> [Cannot be reached] "Enabled persistence"
--> "Begin encrypting files"
--> "Display Ransom notices"
--> "Continue encrypting any new files"
--> "Attempt to spread via SMB port 445"
Endif
Malware Composition
WannaCry or in this instance Ransomware.wannacry.exe is a single binary that executes on the system and creates all necessary assets on the system for encryption of all files.
1
2
3
4
5
6
7
8
9
10
11
skin rose
skinparam componentStyle uml2
class WannaCry {
Creates MS Service for persistence
..
Unpack resources for Ransom notice
..
Encrypt files
}
Analysis
Basic Static Analysis
| HashType | Sum |
|---|---|
| md5 | DB349B97C37D22F5EA1D1841E3C89EB4 |
| sha1 | E889544AFF85FFAF8B0D0DA705105DEE7C97FE26 |
| sha256 | 24D004A104D4D54034DBCFFC2A4B19A11F39008A575AA614EA04703480B1022C |
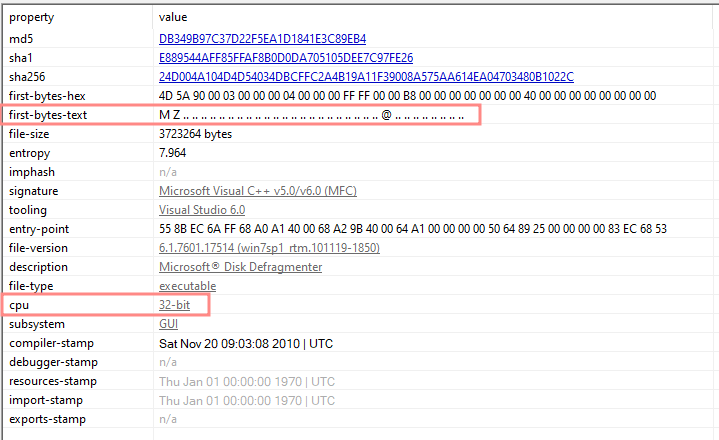
32-bit Portable Executable
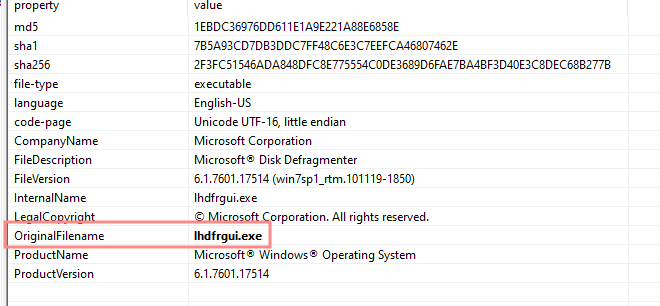
Original filename of sample:
lhdfrgui.exe
Interesting Strings
The following strings in the binary have been found noteworthy:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
%s -m security
C:\%s\qeriuwjhrf
C:\%s\%s
tasksche.exe
icacls . /grant Everyone:F /T /C /Q
\\172.16.99.5\IPC$
\\192.168.56.20\IPC$
WanaCrypt0r
WANACRY!
mssecsvc.exe
cmd.exe /c "%s"
DeleteCriticalSection
attrib +h .
There were also four references to:
1
!This program cannot be run in DOS mode.
This could be an indication that there are other, complete binaries in the package.
Basic Dynamic Analysis
No Internet Detonation
At execution, queries are being made to domains:
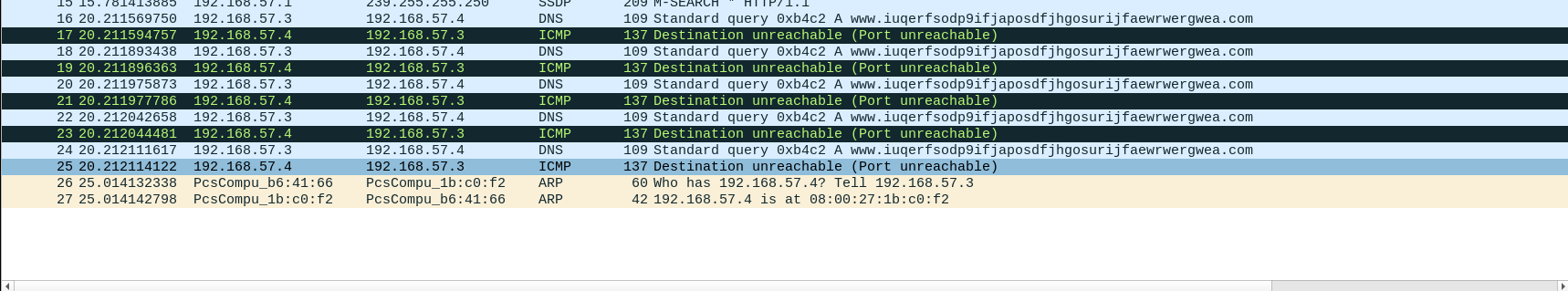
In particulr:
www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com: type A, class IN
Constant checking of connection
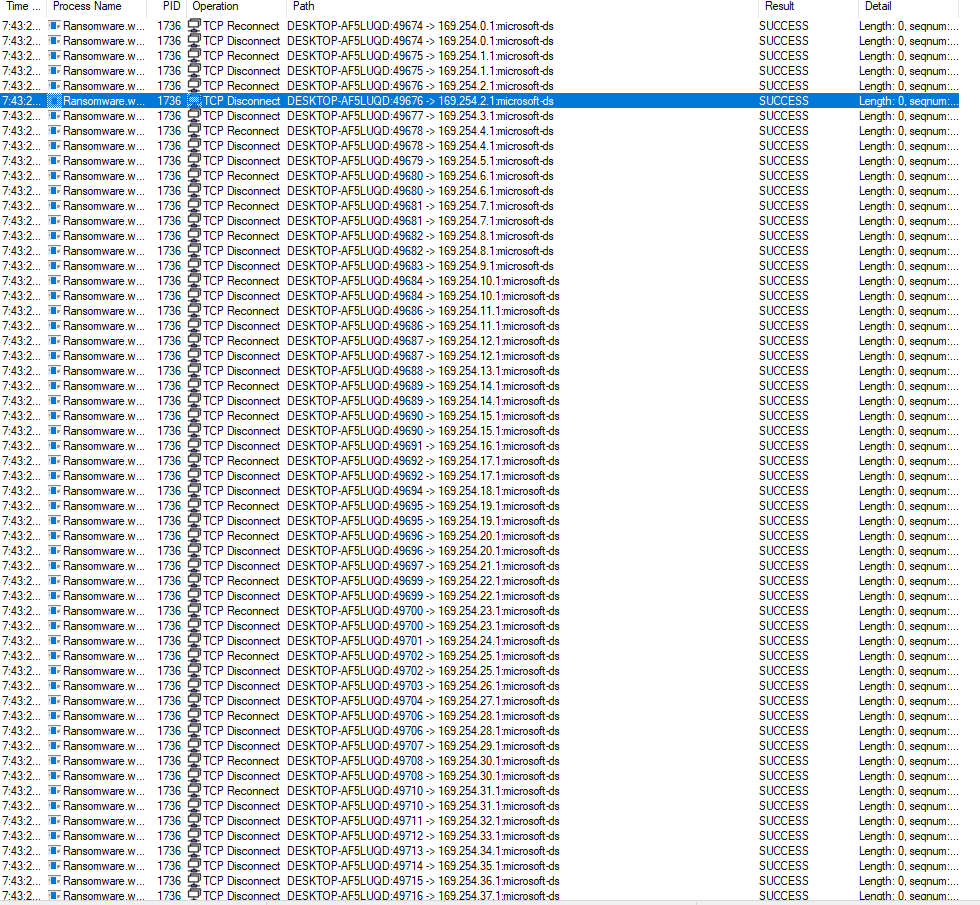
Is this querying for NFS and SMB shares?

WannaCry popup comes back if you close it
Internet Detonation
DNS Queried Succeessfully > executes GET against http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
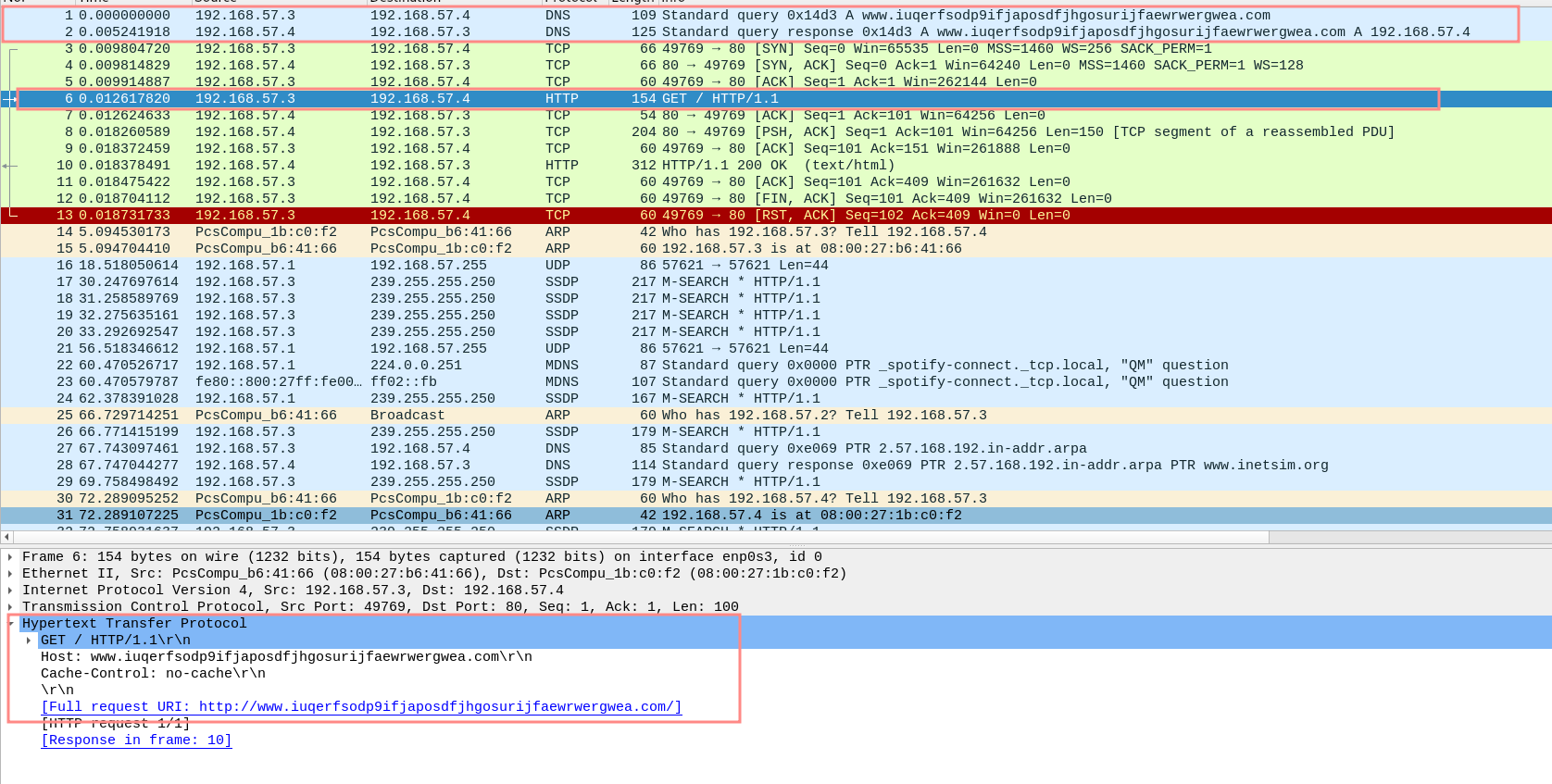
Advanced Static Analysis
Kill Switch

InternetOpenA prepares the application for future calls (Source: https://learn.microsoft.com/en-us/windows/win32/api/wininet/nf-wininet-internetopena)
InternetOpenUrlA tests the connection to www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com using the call:
If it can, reach the destination, the program calls InternetCloseHandle to end the internet connection and returns out without malicious action
If the Kill Switch is not activated
fcn.00408090 is called
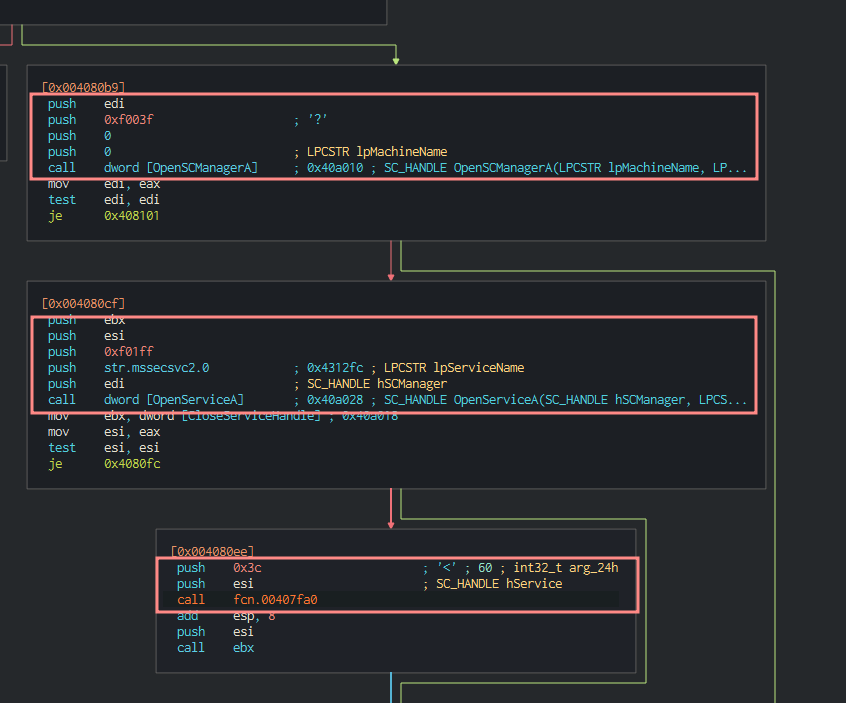
Reaching for persistence
ChangeServiceConfig2A is often used to change service properties and allow malware to persist.
This is WannaCry’s pathway to calling ChangeServiceConfig2A.
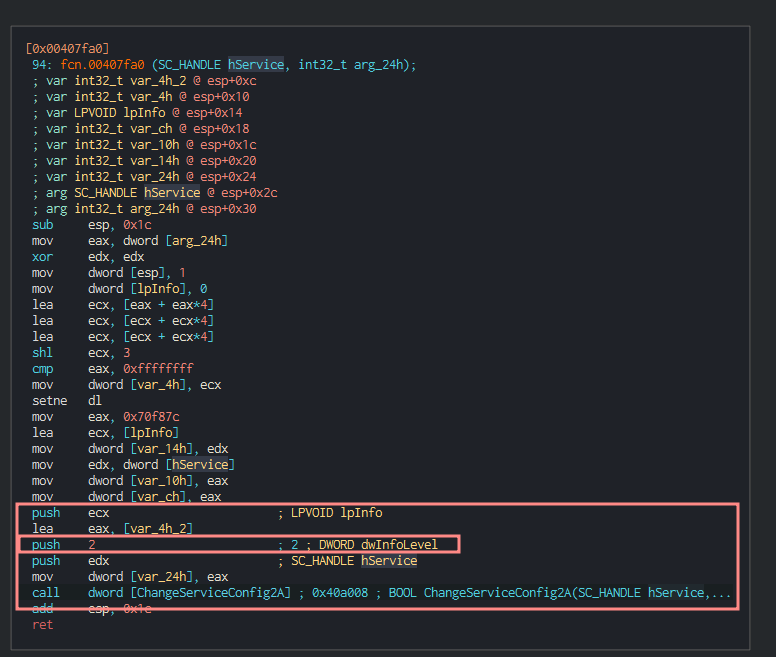
Encryption of files
The following seems to be the pathway to looping through all files and begining the encrytion process.
Execute fcn.00407f20
Which creates a Microsoft Security Center Service, if it can open OpenSCManagerA
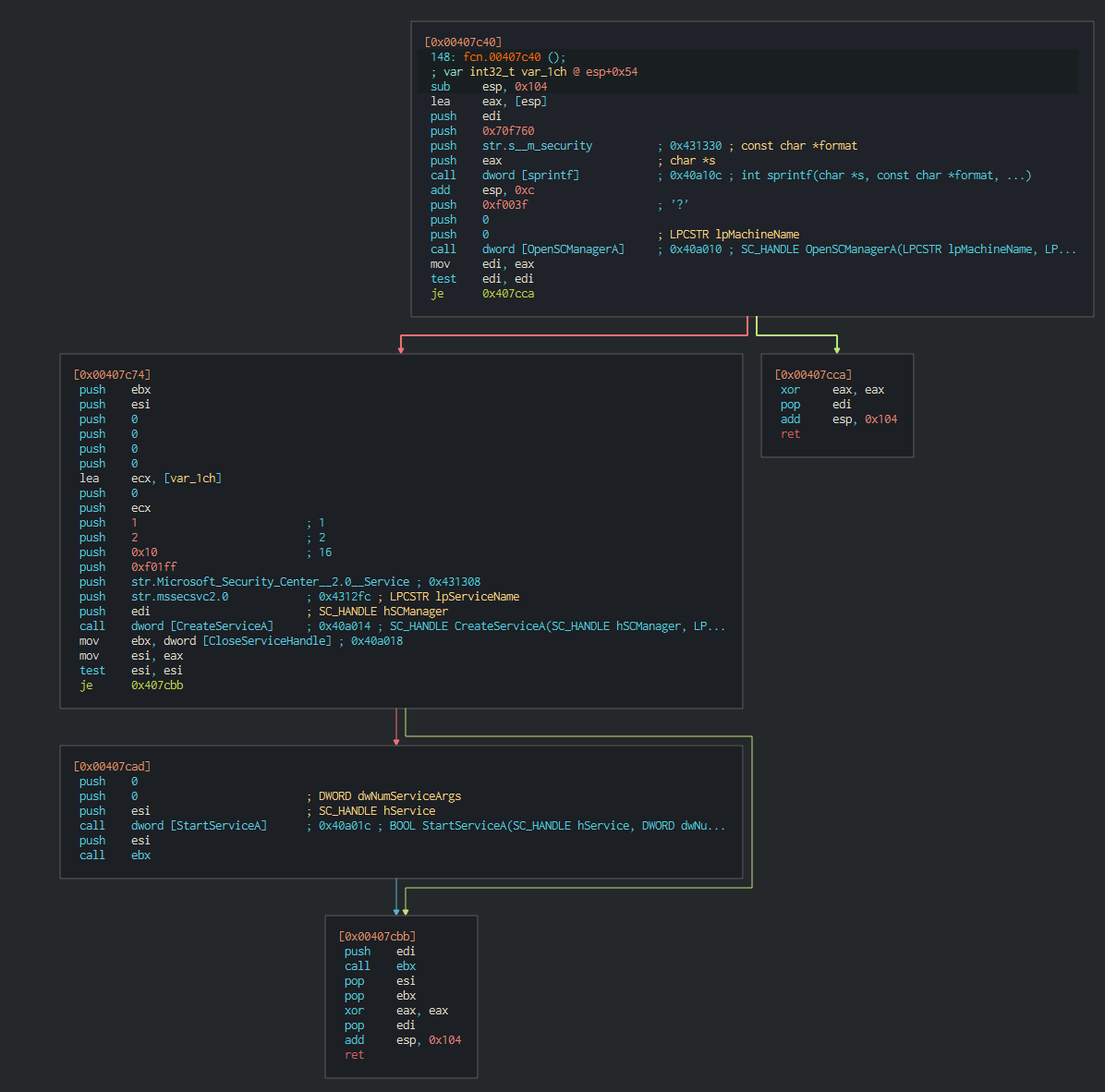
Then proceed to encrypting files
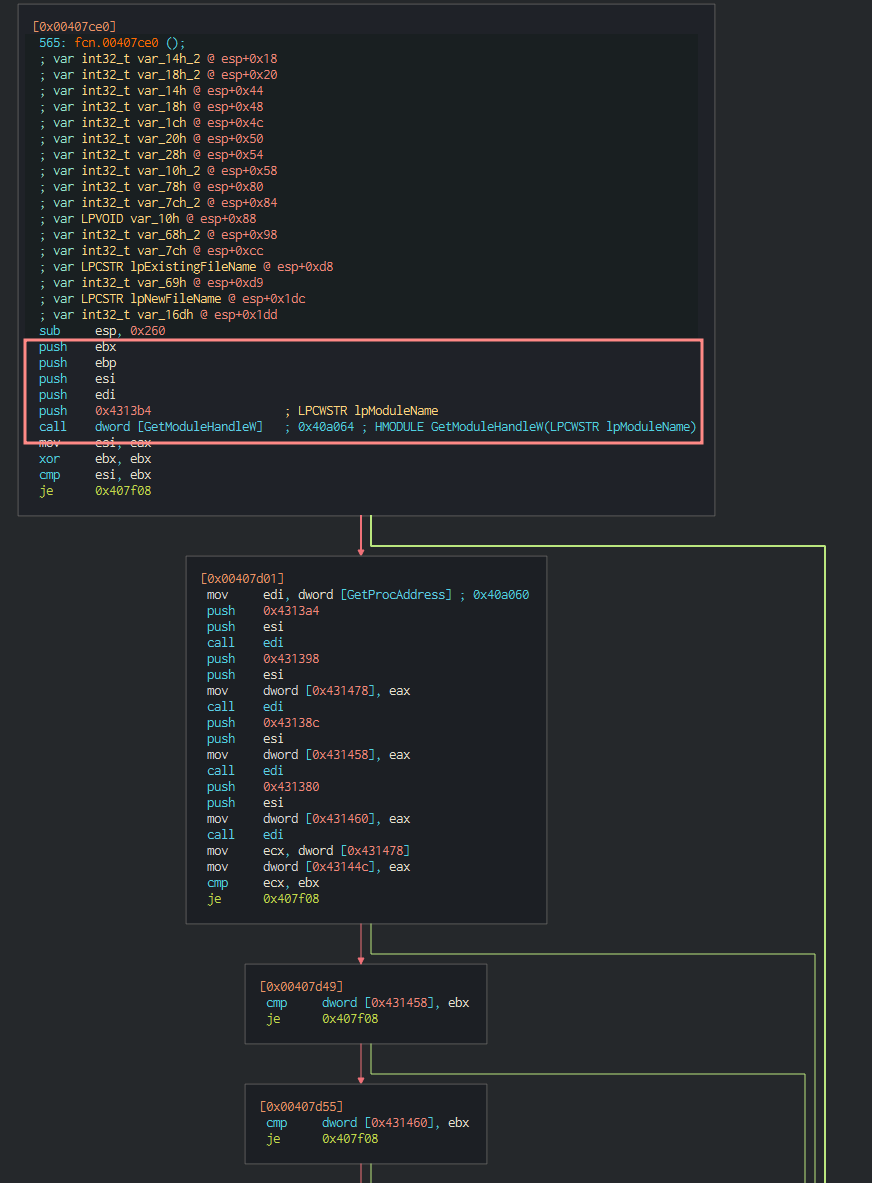
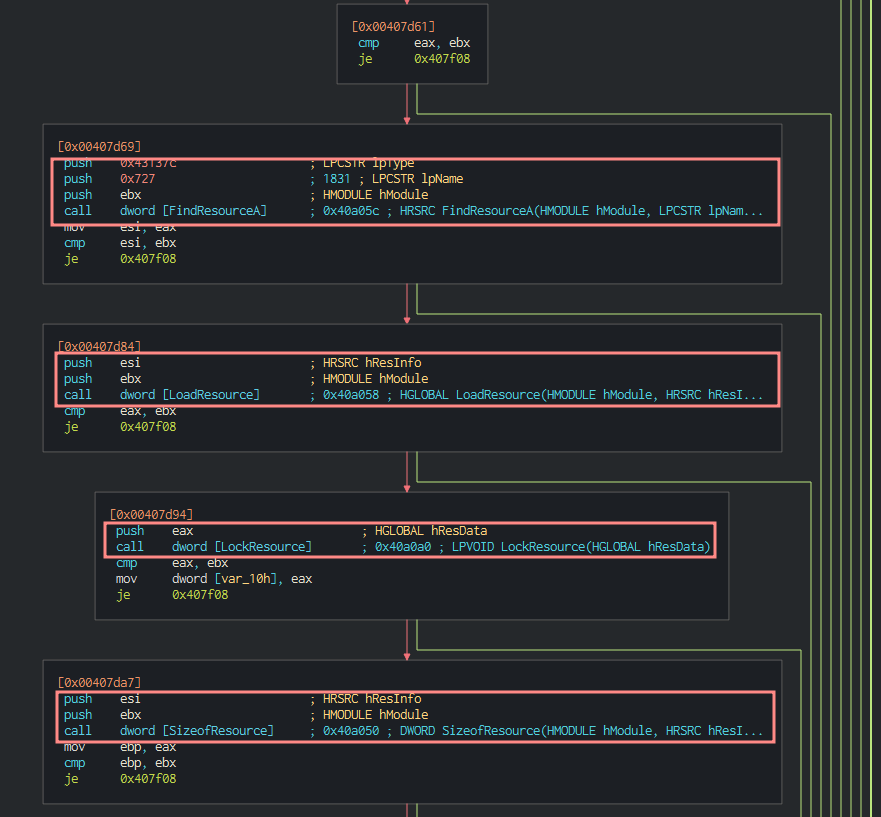
Finding, loading, locking and analyzing the size of resources
Moving them to their new file extension
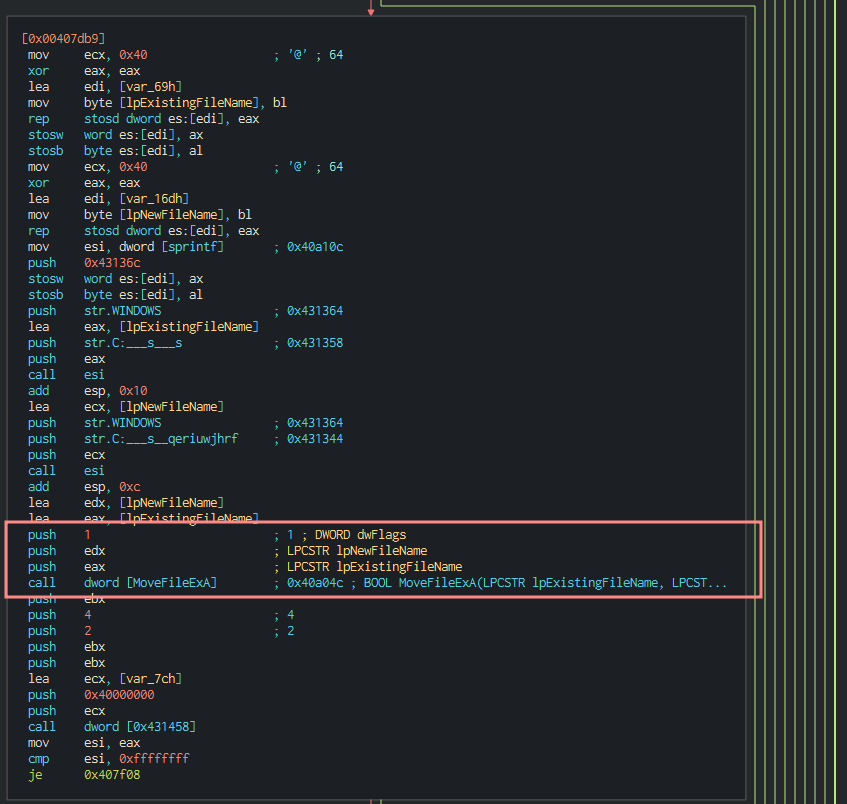
Encrypt.
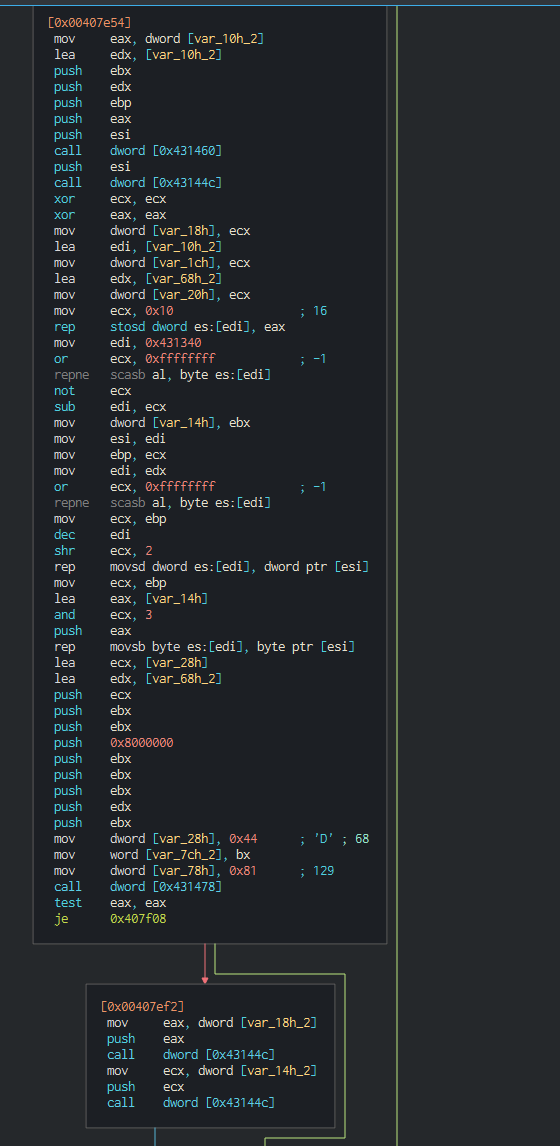
Advanced Dynamic Analysis
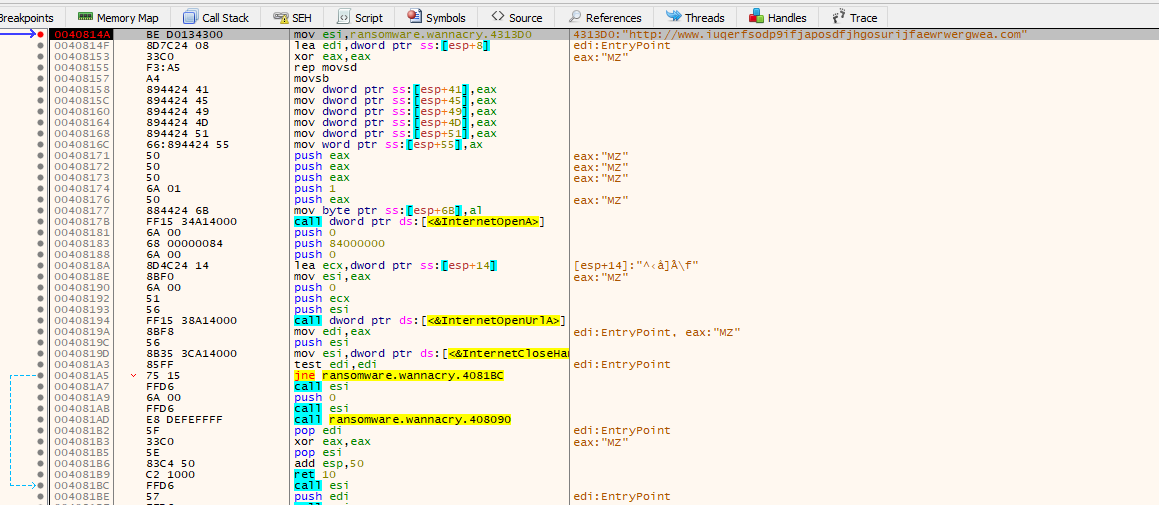
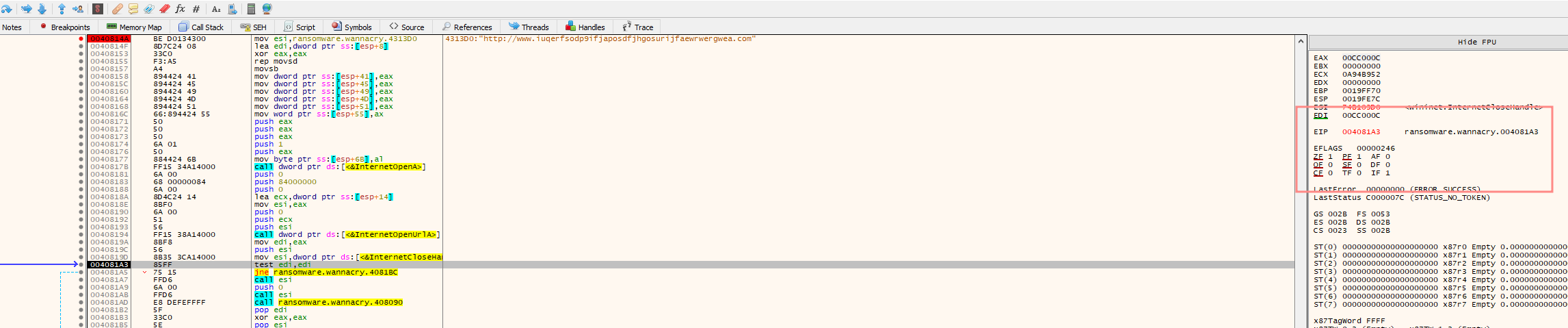
Because the test edi, edi/ call to open the InternetURL was successful ZF is 0
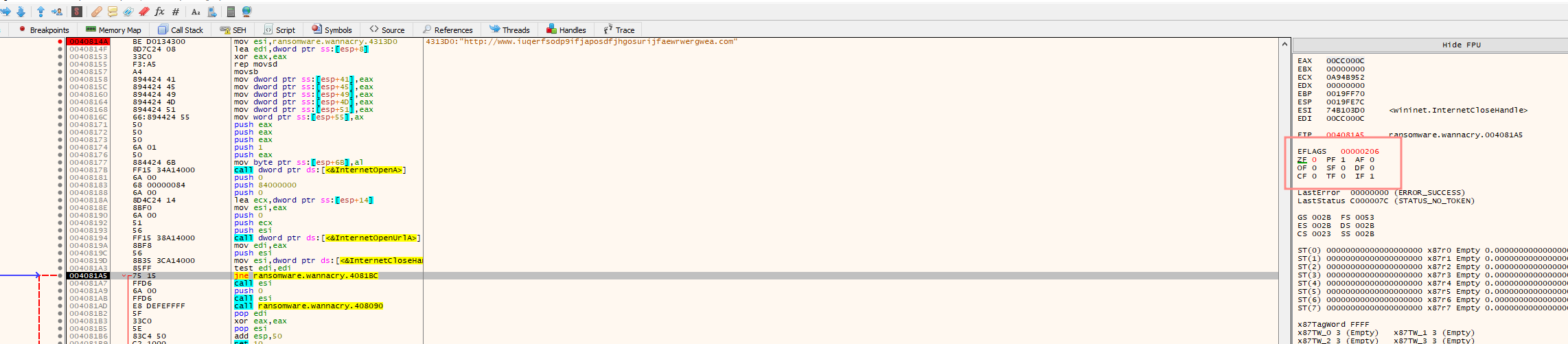
Flipping that to 1 allows for the execution of the ransomware to happen, despite INetSim being up
Indicators of Compromise
Network
GET against http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
Checking for networked SMB shares

Host-based
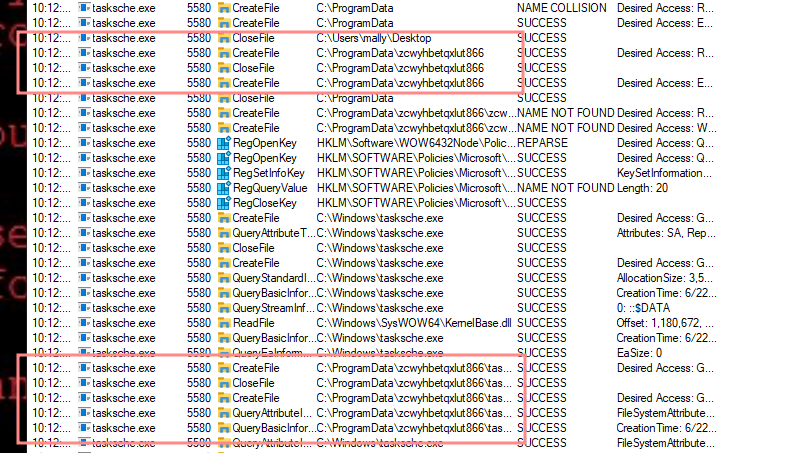
Hidden folder:
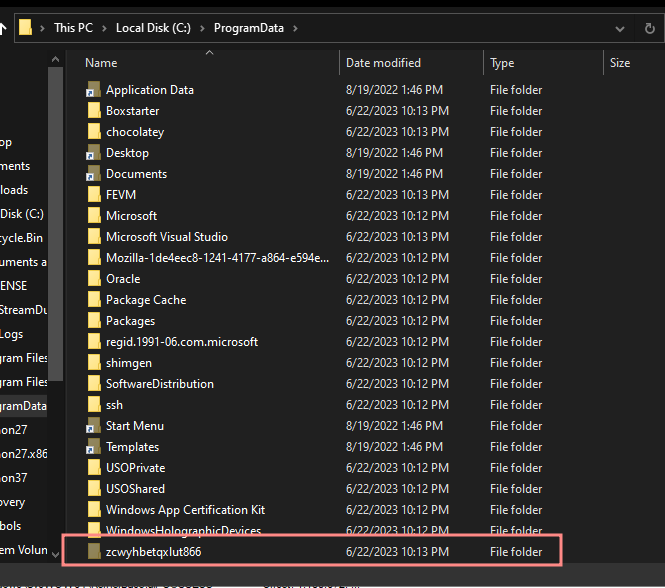
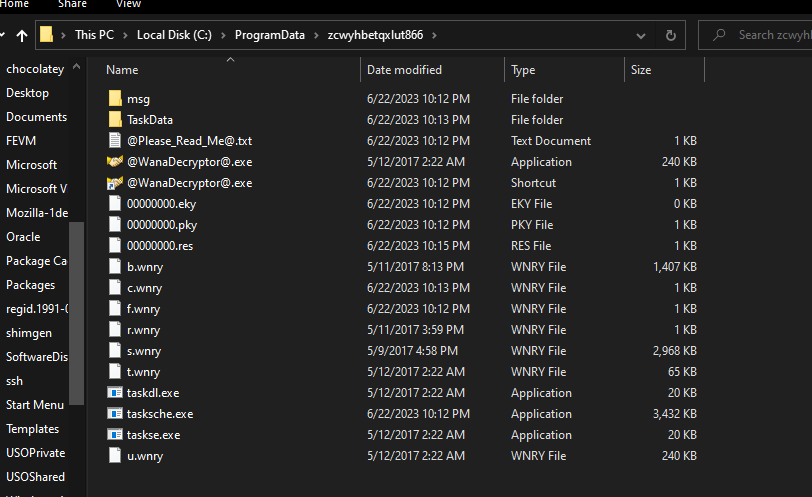
Looks like staging environment:
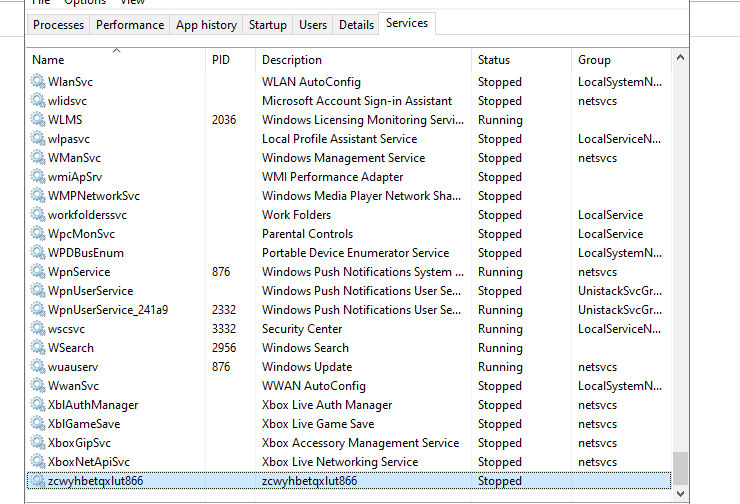
Also now a service – likely to encrypt that is added to the OS after detonation
YARA Rule
Below is a YARA rule that show be able to identify WannaCry in your environment.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
rule WannaCry {
meta:
last_updated = "2023-06-25"
author = "close"
description = "YARA rule for WannaCry"
strings:
$wanacryptor = "WanaCrypt0r" wide
$wanacry = "WANACRY!" fullword
$msseccenter = "mssecsvc.exe" fullword
$filepermissions_all = "icacls . /grant Everyone:F /T /C /Q" fullword
$killurl = "www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com" fullword
$tasksche = "tasksche.exe" fullword
$smb1 = "\\\\172.16.99.5\\IPC$" wide
$smb2 = "\\\\192.168.56.20\\IPC$" wide
$templatedpath = "C:\\%s\\qeriuwjhrf"
$hidden_folder = "attrib +h ."
$PE_magic_byte="MZ"
condition:
$PE_magic_byte at 0
and $wanacryptor
and $wanacry
and $msseccenter
and $filepermissions_all
and $killurl
and $tasksche
and $smb1
and $smb2
and $templatedpath
and $hidden_folder
}
